Tekniken har förändrat vårt sätt att arbeta, kommunicera och våra finansiella processer. Företag och konsumenter använder papperspengar i allt mindre utsträckning. De ger plats för kontaktlösa betalningar. Konsumenterna använder mobiltelefoner för att betala för varor på nätet. Under 2009 dök en ny typ av betalningssystem upp - digitala pengar. Överföringar registreras i en offentlig blockkedja som alla har tillgång till. Det är så säkerheten för kryptovaluta säkerställs. Det är en komplicerad process, men resultatet är en digital huvudbok med transaktioner som hackare inte kan hacka.
Vad påverkar säkerheten för kryptovalutor
Centraliserade onlinebörser ger inte samma nivå av skydd för pengar som en bank. Varje månad finns det publikationer om hacking av handelsplattformar eller nya metoder för att lura godtrogna användare. För att undvika att vara bland dem är det viktigt att känna till de grundläggande principerna för skydd mot angripare och de sårbarheter de använder för att komma åt konton.
Lagring av kryptovaluta
Blockchain gör digitala tillgångar motståndskraftiga mot hacking. Det gör att du kan köpa och investera i kryptovaluta på ett säkert sätt. Allt fler bedrägerier riktas dock mot deltagarna snarare än mot själva systemet. Det finns risker som måste hanteras av kunderna:
- Sårbarheten hos mynt och symboler som lagras på börsen gör dem mer tillgängliga för hackare.
- Phishing-attacker via e-post där den ursprungliga webbplatsen ersätts av en falsk.
- Bedrägerier som går ut på att ändra mobiltelefonnummer för att knäcka tvåfaktorsautentisering.
Kalla och varma plånböcker
Skillnaden i hur tokens och mynt lagras ligger i säkerhetsnivån för kryptovaluta. Appar och skrivbordsprogram gör att du kan skicka och ta emot kryptovaluta som ett digitalt bankkonto för fiat-tillgångar:
| Varmt | Mobila appar |
| Skrivbordsprogram | |
| Onlinetjänster (Binance, Blockchain.com) | |
| Kall | USB-enheter där nycklar lagras i krypterad form |
| Plånböcker av papper |
Onlineplattformar är mycket populära eftersom de är lätta att sätta upp och använda. När ett konto skapas på en börs via en mobilapp eller på en dator har användaren en varm plånbok. Denna typ av lagring är bekväm för vardagliga transaktioner. Eftersom hot wallets är anslutna till internet är det lätt att göra transaktioner. Du behöver bara trycka på några knappar på din mobiltelefon eller dator.
5020 $
bonus för nya användare!
ByBit ger bekväma och säkra villkor för handel med kryptovalutor, erbjuder låga provisioner, hög likviditetsnivå och moderna verktyg för marknadsanalys. Den stöder spot- och hävstångshandel och hjälper nybörjare och professionella handlare med ett intuitivt gränssnitt och handledning.
Tjäna en 100 $-bonus
för nya användare!
Den största kryptobörsen där du snabbt och säkert kan börja din resa i kryptovalutornas värld. Plattformen erbjuder hundratals populära tillgångar, låga provisioner och avancerade verktyg för handel och investering. Enkel registrering, hög transaktionshastighet och tillförlitligt skydd av medel gör Binance till ett utmärkt val för handlare på alla nivåer!
Hot plånböcker är lätta att använda, men de har en nackdel - hög sårbarhet. Till exempel kan växlingskonton inte rekommenderas för lagring av stora mängder kryptovaluta. Detta utsätter besparingarna för potentiella säkerhetshot, hackerattacker.
För långsiktiga investeringar är kalla plånböcker lämpliga. Denna metod anses vara så säker som möjligt, eftersom de inte är anslutna till internet och risken för hackning minskar. Exempel är papper med nycklar tryckta på eller hårdvaruenheter. Separata fysiska medier (vanligtvis i form av ett USB-minne) används också aktivt för att lagra privata nycklar, vilket gör dem osårbara för hackare och bedragare.
Frö-fras
Den grundläggande principen för kryptovaluta är idén om decentralisering. Användare får ett konto utan att verifiera sin identitet. De behöver inte förlita sig på en bank eller annan plattform för säker lagring. Digitala valutor använder blockchain för att göra detta. Den skyddar dem med ett peer-to-peer-nätverk av datorer på olika platser som lagrar kopior av all data. Men decentralisering har en nackdel.
Om nyckeln går förlorad kan användaren inte kontakta helpdesk för att få en ny kod. För detta ändamål används en fröfras (en lista med ord som genereras av programmet som ger tillgång till digitala pengar). Dess närvaro gör att du kan få kontroll över ditt personliga konto även vid plånboksförlust.
Tillförlitliga utbyten
Handelsplattformar lagrar kunddata i krypterade valv.
Den största uppmärksamheten i valet ägnas åt:
- Anseende. Bekanta dig med börsens historia, kontrollera fall av hacking.
- Existensens varaktighet. Långt arbete fungerar som en indikator på motståndskraft mot hackerattacker och bedrägerier.
- Handelsvolym. Hög intensitet i verksamheten talar för popularitet.
Tekniska sårbarheter
Blockkedjetekniken utvecklas, men den digitala valutan är inte immun mot hackerattacker. Det finns cybersäkerhetsrisker som är viktiga att vara medveten om. Vissa stora företag har redan drabbats av hackare och andra attacker från illasinnade aktörer.
Virus
Kriminella använder ofta skadlig kod som kopierar all information som skrivs in från tangentbordet. Den skickas sedan vidare till hackare för att de ska få tillgång till webbplatser där kryptotillgångar lagras.
Hackning av en plånbok eller börs
Sedan digital valuta började användas har många stora företag drabbats av bedrägerier:
- BitGrail. En börsplattform som förlorade $146 miljoner under 2018 på grund av en sårbarhet i sina servrar.
- KuCoin. En kryptobörs som drabbades av en attack från hackare. Den totala skadan uppgick till mer än $200 miljoner.
- MtGOx. En av de första kryptoplattformarna. Efter att ha förlorat $450 miljoner upphörde plattformen att existera.
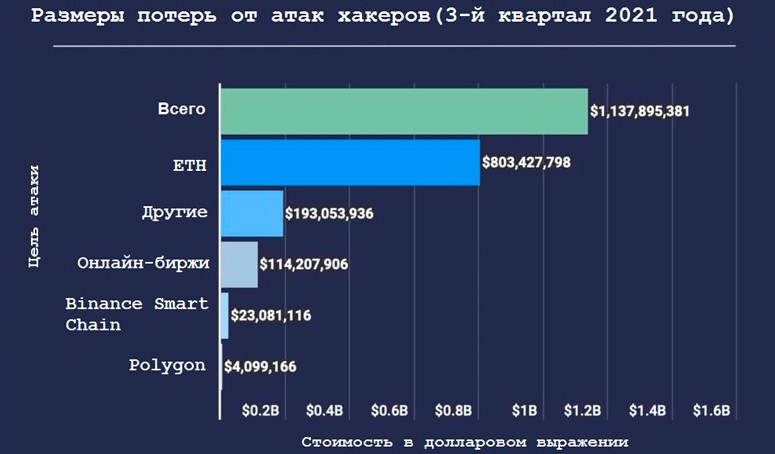
Fall av hackning av en programplånbok är inte registrerade för tillfället. Men om hackare lyckas få information från användaren (hemlig fras, wallet.dat-fil eller lösenord) är det inte svårt för dem att få tillgång till det personliga kontot.
Falska appar
Problemet med dolda gruvarbetare är vanligt i den officiella Google Play och App Store. Det här är skadliga program som smygande bryter block för offret och överför belöningen till hackare. Fall där bedragare försökte distribuera falska applikationer är inte isolerade. Programvaran kopierade helt designen och funktionaliteten hos officiella plattformar. Alla uppgifter som användaren har angett kan stjälas av angripare för att ta kontroll över plånboken.
Bedrägliga plattformar
Ett av sätten att beslagta offrets pengar är att imitera arbetet med ett kryptobörs. Ofta på sådana falska tjänster erbjuds kunderna stor funktionalitet med mycket låga provisioner, plattformen får hög popularitet bland samhället. När en stor mängd visas på kontona överför hackare pengarna till sina plånböcker och stänger webbplatsen. Detsamma gäller kryptovalutapyramider som erbjuder mycket höga vinster. I verkligheten utförs inga investeringsoperationer, bedragarna stjäl kundernas pengar.
Nätfiske
Detta är en uppsättning åtgärder från hackare, vars huvudsakliga syfte är att få konfidentiell information. Angripare gör kopior av officiella stora webbplatser, till exempel Binance. Länkar till phishing-resurser distribueras genom att skicka meddelanden via e-post och sociala nätverk. Mindre ofta används SMS till en mobiltelefon. Offret, utan att märka spoofing, överför namnet, lösenordet och den privata elektroniska nyckeln själv.
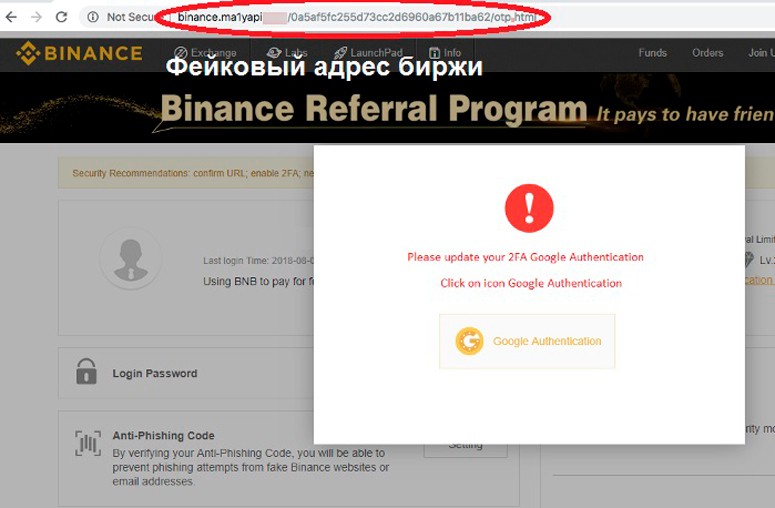
Falska konton på sociala nätverk
Med teknikens utveckling har människors kommunikation blivit tillgänglig via budbärare och tjänster för kommunikation. Hackare drar nytta av detta genom att skapa falska sidor.
Förklädda till kända offentliga personer eller företagssupport försöker bedragarna etablera kontakt och få information. Deras mål är bankkortsnummer, plånboksadresser och lösenord. Ibland ber de att få överföra en summa pengar till sitt personliga konto under täckmantel av ett falskt konto.
Den mänskliga faktorn
Miljontals bitcoins ligger på plånböcker som tillgången aldrig kommer att återställas till. Och detta har inget att göra med hackarnas handlingar.
Förlust av lösenord
Varje år växer antalet "glömda" digitala mynt. Den första platsen bland orsakerna till detta är förlusten av ett lösenord. Eftersom kryptovaluta fungerar på blockchain och den privata nyckelfilen är krypterad med SHA-256-algoritmen är sannolikheten för att återställa åtkomst nära noll. Det finns speciella tjänster som kan plocka upp lösenordet. Denna metod är lämplig för de användare som kommer ihåg åtminstone en del av den, men du måste betala en stor summa för arbetet. Om klienten glömde hela lösenordet och inte sparade fröfrasen kommer pengarna att gå förlorade.
Felaktig adress till mottagaren
Transaktioner med digitala valutor är irreversibla. Detta innebär att det är omöjligt att returnera skickade tokens och mynt. En felaktig adress eller fel mottagarnätverk kommer att leda till en fullständig förlust av medel. Olika blockkedjor är vanligtvis inte kompatibla med varandra. Därför bör kryptotillgångar endast skickas till en adress som är lämplig för typen av pengar.
Många plånböcker har redan en adressverifieringsfunktion. De kan varna ägaren om ett fel, men sådana applikationer verifierar inte mottagarens namn. Om pengar skickas till någon annans plånbok kommer de att gå förlorade.
Grundläggande tips för säkerhet kring kryptovalutor
I takt med att det decentraliserade systemet växer får användare som befinner sig långt från den digitala världen tillgång till kryptomarknaden. I vissa delar av världen används bitcoin redan som ett betalningsmedel som liknar papperspengar. Du bör komma ihåg de rekommendationer som gör det möjligt för ägaren att behålla tillgången till plånboken.
Använd endast betrodda tjänster
Många företag har arbetat på kryptomarknaden i mer än ett år och har ett gott rykte. När du ansluter till välkända plattformar minimeras risken för att bli hackad. Du bör noggrant kontrollera länkarna som användaren går till webbplatsen på. Om de skiljer sig till och med ett tecken från resursens officiella adress, bör du omedelbart lämna sidan.
Förvaring av kryptovaluta på olika plånböcker
Att dela upp kapitalet i ytterligare delar är inte bara en fråga om bekvämlighet utan också säkerheten för digitala mynt. Att fördela hela beloppet till flera valv gör att du kan spara det mesta av pengarna om du förlorar kontrollen över ett. Heta plånböcker används om användaren gör många transaktioner, men det är inte säkert att använda dem för stora summor. Kalla är mindre praktiska, men de är mer motståndskraftiga mot hackersattacker.
QR-koder när du skickar kryptovaluta
Överföring av uppgifter är en komplicerad del av betalningsprocessen med polletter och mynt. En adress är en post med bokstäver och siffror (27 till 34 tecken). Mottagaren av betalningen måste tillhandahålla denna långa uppsättning till den person som gör transaktionen. För att minska felen och förbättra användbarheten kan du konvertera adressen till QR-kodformat.
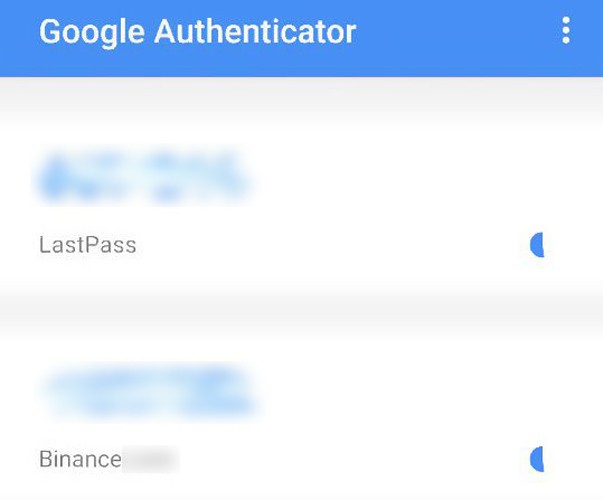
Tvåfaktorsautentisering
2FA är ett extra lager av kryptovalutasäkerhet. Det gör att du kan se till att klienten själv försöker komma åt kontot. Först måste ägaren ange sitt namn och lösenord. Sedan får användaren ett unikt lösenord på sin mobiltelefon eller e-post. Google Authenticator-applikationen blir en populär metod för 2FA på stora handelsplattformar för kryptovaluta. Tjänsten genererar automatiskt auktoriseringskoder och överför dem till användarens smartphone.
Starka lösenord
För att skydda mot hackning bör slumpmässiga (inte relaterade till ägarens personuppgifter) kombinationer av symboler, bokstäver och siffror i olika register användas. De låter dig säkerställa säkerheten för kryptovaluta. Det rekommenderas att ställa in unika lösenord för olika resurser.
Decentraliserade börser
Det är plattformar där deltagarna byter digitala pengar utan mellanhänder med hjälp av direktöverföring (P2P). Den största fördelen är att tokens innehas direkt av ägaren tills transaktionen är genomförd. Detta uppnås genom att använda smarta kontrakt. Hög anonymitet på DEX-utbyten beror på bristen på identitetsverifieringsprocedur. Den största nackdelen - det är vanligtvis omöjligt att köpa eller sälja kryptovaluta i utbyte mot fiat-pengar.
Offentligt Wi-Fi
Många mobiltelefoner har en funktion som gör att de automatiskt ansluter till publika nätverk. Angripare kan stjäla data (namn, lösenord, privata nycklar) eller ladda ner skadlig kod. En bra lösning är att sluta söka efter Wi-Fi efter att ha lämnat jobbet eller hemmet. Om du behöver få din enhet online snabbt är det bäst att undvika offentliga hotspots och aldrig skicka känslig information via någon annans internetanslutning.
Sökfält i webbläsaren
För att kontrollera om din anslutning till en webbplats är säker bör du kontrollera adressen till sidan. För att bekräfta äktheten och säkerheten för dataöverföringskanalen används speciella SSL-certifikat. Om de inte är installerade, eller om utgångsdatumet har gått ut, kan webbläsaren meddela användaren om detta och blockera övergången till länken. Det är inte säkert att skicka information och gå till en sådan webbplats.
Gratis giveaways för kryptovalutor
Sådana kampanjer kallas AirDrop. De organiseras av offentliga nystartade företag eller stora börser när de lanserar en ny bransch. Du kan få gratis mynt för att utföra enkla uppgifter:
- Publicera ett inlägg i sociala medier för din räkning.
- Bli en ny användare av plattformen.
- Genomför några transaktioner på den.
Men under täckmantel av luftdroppar, bedrägliga system används ofta. Om en sådan åtgärd initieras av en okänd arrangör, och den ber dig att överföra pengar, är det troligt att det är skadligt.
Sammanfattning
Kryptovaluta är en säker tillgång med en hög nivå av motståndskraft mot hacking. Hackerattacker riktas oftast mot plånboksinnehavare snarare än systemsårbarheter. Innehavare av digitala pengar måste vidta försiktighetsåtgärder för att hålla kryptovalutan säker:
- Aktivera tvåfaktorsautentisering i kontoinställningarna på växlar.
- När du klickar på länkar, kontrollera sidadressen för att undvika nätfiske.
- Dela inte med dig av lösenord eller annan konfidentiell information till tredje part.
- Förvara säkerhetskopior av nycklar på medier som inte är anslutna till Internet.
- Använd kalla plånböcker för att samla på dig stora mängder digitala pengar.
Trots att börser och växlare kämpar mot bedragare beror kryptovalutans säkerhet mer på ägarna av tokens och koins. Om användarna följer enkla regler ökar säkerheten för deras data.
Vanliga frågor och svar
✅ Kan en bedragare kringgå tvåfaktorsautentisering?
Ja, hackare kan avlyssna ett textmeddelande eller ett e-postmeddelande. För att undvika detta är det bäst att använda Google Authenticator-appen. En angripare kan också ringa offret, presentera sig som en kundtjänstrepresentant och be om verifieringskoder.
❕ Hur skiljer man en gratis myntutdelning från ett bedrägligt system?
Det finns speciella webbplatser där information om kampanjer från kryptovalutautvecklare visas. Om inbjudan kom till posten eller telefonen, och förskottsbetalning för deltagande krävs, och det finns ingen information om arrangören i samhället, troligen är det skadligt.
❓ Vad ska man göra om en användare går till en nätfiskewebbplats och anger sina uppgifter?
Om kontoägaren insåg att tjänsten är en kopia av den riktiga, är det nödvändigt att ändra lösenord till e-post, konto, ändra verifieringsfrågan. All information som kan ge en hackare tillgång till ett personligt konto bör uppdateras.
💻 Hur skyddar du din dator och mobiltelefon från hackning?
Uppdatera regelbundet officiell programvara, håll ett öga på övergångslänkarna i din webbläsare, installera den senaste versionen av antivirusprogrammet.
❔ Vad händer om en seedfras går förlorad?
Om den hemliga listan med ord går förlorad kommer du inte att kunna återställa tillgången till din plånbok. För att ytterligare säkra frasen applicerar användarna den på ett hållbart material.
Ett misstag i texten? Markera det med musen och tryck på Ctrl + Ange
Författare: Saifedean Ammous, en expert på kryptovalutans ekonomi.















