Most online resources that a user visits collect personal information about their visitors. This is in the form of cookies – small fragments of data transmitted to the site from the browser. By clicking on the “Allow collection” button, the user gives their consent, and the developers legally receive IP-address, search queries and device parameters. This data is needed for statistics on the effectiveness of the site and for future targeted advertising. The services can also transfer this information to third parties.
What are anti-detection browsers?
Google Chrome, Opera and other popular Internet explorers take data for their own analytics, if the user allows the collection of information when installing the browser. In rare cases, this can happen covertly. However, there are ways to keep personal information secret. For this purpose, antidetect browsers (antidetect browser, antics) were created.
Principle of operation
In essence, these are ordinary Internet explorers. However, one of the main points in their work is masking the digital footprint of the user. Anti-detect browsers transmit different from the real data and hide the activity of users. They can be used to substitute different information: IP address, operating system, screen resolution and other parameters.
Several technologies have been created for privacy. They are listed below:
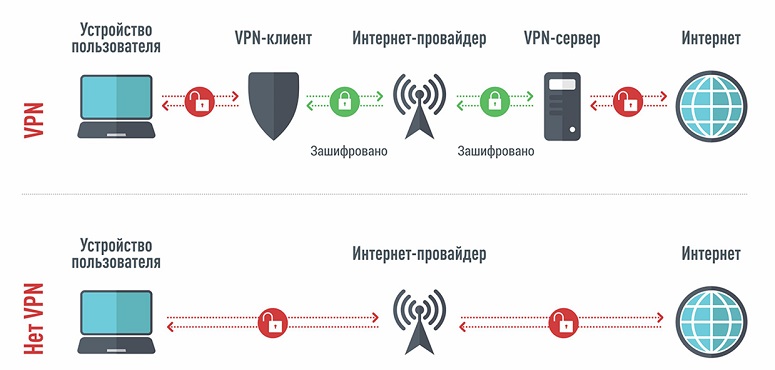
- Virtual personal networks (VPN). The technology creates an encrypted connection between a computer and a server. As a result, the user visits the Internet, but the IP address of the remote equipment is transmitted.
- Proxy servers (Proxy). They work as intermediaries between the user and the network. Requests and responses are sent first to the proxy servers and only then to the source computer.
- The Onion Router (TOR). The technology works on the principle of forwarding data through several nodes before it reaches its destination. Each node only knows about the previous and next node. It does not have access to the start and end points. This makes it difficult to track data.
- Cryptographic encryption. In it, information does not need to be spoofed or transferred between different nodes. The data moves as an encrypted hash that is difficult to decode. The same principle works in digital currencies.
Anti-detect browsers can either use one of the technologies or combine them in combinations. This gives more opportunities for secrecy and makes it harder for external observers to collect data.
5020 $
bonus för nya användare!
ByBit ger bekväma och säkra villkor för handel med kryptovalutor, erbjuder låga provisioner, hög likviditetsnivå och moderna verktyg för marknadsanalys. Den stöder spot- och hävstångshandel och hjälper nybörjare och professionella handlare med ett intuitivt gränssnitt och handledning.
Tjäna en 100 $-bonus
för nya användare!
Den största kryptobörsen där du snabbt och säkert kan börja din resa i kryptovalutornas värld. Plattformen erbjuder hundratals populära tillgångar, låga provisioner och avancerade verktyg för handel och investering. Enkel registrering, hög transaktionshastighet och tillförlitligt skydd av medel gör Binance till ett utmärkt val för handlare på alla nivåer!
Why privacy is important
User information is analyzed for more than just useful purposes. The history of requests and digital footprint allows to create a fairly complete dossier about the personality of the Internet surfer, his tastes, lifestyle and even financial transactions.
A shopping list tells a lot about the composition of the family. Delivery service pickup points – about the place of residence or work. Travel inquiries and ticket monitoring reveal when the user may be away. Such information is also used for illegal purposes.
Security in digital assets and crypto-payments
Financial transactions are also at risk. Both transactions in the traditional system and payments in cryptocurrencies can be transmitted surreptitiously.
The advantage of digital money on the blockchain is its decentralization. In other words, no intermediaries (e.g. banks) are needed for transfers. However, this also means that users are responsible for the security of financial transactions themselves.
Anti-detect browsers can increase the privacy of transactions and cryptocurrency balances. They make tracking and identification much more difficult and therefore less vulnerable to hacker attacks. The benefits of anti-detect browsers are as follows:
- Anonymous transactions. When making cryptocurrency transactions, an anti-detect browser hides identity and geo-position data, which increases the level of secrecy. In conjunction with mixers and transfers in sensitive assets (e.g. Monero), revealing the identity of the holder becomes virtually impossible.
- Censorship bypass. In some countries, access to cryptocurrency platforms is restricted or banned – for example, in China. Such browsers help to bypass censorship, trade and exchange digital assets.
Choosing an anti-detection browser
Several browsers with a high degree of privacy are implemented in August 2023. The ranking of the most popular ones is presented in the table.
| Place | Namn | Funktioner |
|---|---|---|
| Browser protects against tracking, monitoring and recognizing users, and also gives you control over cookies and cache settings. A special feature of the explorer is the work with several profiles at the same time (up to 1 thousand). This differentiates personal and financial goals, which helps to avoid links between different activities. | ||
| Each tab in explorer runs in a separate container. This helps prevent data overlap and increases security. | ||
| The browser works on the basis of onion routing technology. It also gives access to resources on the Tor network with .onion domain names. The main disadvantage is the slow page loading speed. | ||
| The software, like many antics, blocks tracking and advertising. Data is transmitted over an encrypted connection and is completely deleted at the end of the session. | ||
| Not the most privacy-conscious browser on the list, it only suspends pop-up ads | ||
| The software is built on the foundation of Chromium. It also has a limited list of privacy features. Mostly blocks tracker systems. | ||
| Replicates Iridium features and Chromium architecture | ||
| Browser is a more secure version of Firefox. Can protect against tracking programs and scripts. | ||
| This is both a browser and a standalone VPN service | ||
| Explorer was created for web developers, but it is used for confidential access to the Internet. The browser has built-in tools for testing sites on different devices and screen resolutions. Explorer blocks ads and tracking. |
Not the most obvious, but the most important benefit is the quality development team behind the product. Users require regular anti-detect browser updates to maintain a high level of privacy.
Creators need to constantly monitor changes in the online space.
To understand how well the team is fulfilling its role, you need to evaluate the browsers on many criteria. These are listed below:
- Data security. You need to evaluate the level of anonymity, as well as the ability to bypass anti-fraud systems. It is important that the team eliminates problems and bugs in a timely manner, releases software updates. A large list of privacy features and technologies can also be an advantage.
- Browser speed and multitasking. Important factors are fast connection and use of web-resources, as well as installation on devices with any operating system (OS) and automation of processes.
- Free application of the browser. Advanced functionality of anti-detection services is usually available by subscription. Some browsers offer a free test period. Dolphin{anty} has a separate basic tariff with a full list of options. It does not need to be paid for.
- A clear interface for novice users. For this purpose, it is important for the team to create navigation of the functionality. Usability-attractiveness also enhances quick access to accounts. Having everyday and familiar tools is a significant plus for the interface. These include creating tags, notes, filters, and choosing a day or night theme.
How to start using the anti-detect browser
To work with antidetect, you need to go through 2 stages – installation and customization of the explorer. For example, the leader of the rating – Dolphin{anty} is used.
The service shows maximum security of data transfer, multitasking and a modern interface. At the first stage, you will need to perform the following actions:
- Go to the official Dolphin{anty} website.
- Create an account (by clicking on the “Register” button).
- Answer the questions for further correct operation of the service.
- Download and install the browser taking into account your operating system. Windows, macOS and Linux versions are available.
- Run and wait for the software to fully load on your computer.
At the second stage, configure connection to proxy servers and VPN networks for additional anonymity. Also regulates the transfer of cookies and the work of saving data in the browser cache. The settings section specifies what information to leave in memory after the end of the session. It is also possible to set a complete data cleanup.
The effectiveness of the anti-detect browser depends on understanding how Explorer works and configuring it properly. The Dolphin{anty} blog has published dozens of guides on how to use the privacy features. For example, “How to set up a browser profile” gives complete instructions on how to create the most secure and anonymous connection.
Ett misstag i texten? Markera det med musen och tryck på Ctrl + Enter.
Författare: Saifedean Ammous, en expert på kryptovalutans ekonomi.















