
In 2017, the first online services for mining digital coins appeared on the Internet. They use an ordinary browser as a mining program, and calculations are performed using users’ processors. Later, the technique was adopted by attackers. In 2021, hidden browser-based cryptocurrency rudarstvo swept the world. Cryptojacking is the illegal mining of digital coins with the resources of users, which the latter are not even aware of.
What is browser mining
Website owners can use the computing power of visitors to mine cryptocoins. In return, users receive rewards or privileges.
The most popular coins for browser mining in 2023 are Monero and Litecoin. These assets are less demanding on PC processing power.
Visitors of Browsermine, Webmining, Getcryptotab and other platforms participate in coin mining voluntarily. Earnings from this activity are small – 50-200 rubles per month, if the computer is turned on around the clock. Profits can be increased by “working” simultaneously on several platforms.
The owners of such sites usually use a small part of the power of clients to avoid hanging pages. Some of them offer visitors ad-free content in return for participating in web mining. If the customer agrees, they give permission to use their PC to mine cryptocurrencies. This is seen as a thank you for the useful content posted on the platform.
Hidden mining in the browser
A website can connect a user to cryptocurrency mining without their knowledge. Fraudsters use the computing power of third-party PCs, and keep the reward for the work done.
5020 $
bonus za nove uporabnike!
ByBit zagotavlja priročne in varne pogoje za trgovanje s kriptovalutami, ponuja nizke provizije, visoko stopnjo likvidnosti in sodobna orodja za analizo trga. Podpira promptno trgovanje in trgovanje s finančnim vzvodom, začetnikom in profesionalnim trgovcem pa pomaga z intuitivnim vmesnikom in učnimi navodili.
Zaslužite bonus 100 $
za nove uporabnike!
Največja borza kriptovalut, kjer lahko hitro in varno začnete svojo pot v svet kriptovalut. Platforma ponuja na stotine priljubljenih sredstev, nizke provizije ter napredna orodja za trgovanje in investiranje. Zaradi preproste registracije, visoke hitrosti transakcij in zanesljive zaščite sredstev je Binance odlična izbira za trgovce na vseh ravneh!
Attackers embed JavaScript code into a website page or plugin that users install for easy access to features. Malware is also installed in pop-up banners or sent via email. Hidden online mining in the browser starts automatically when the site is opened.
Sometimes hackers embed malicious code on the resource page without the administration’s knowledge. This phenomenon is known as cryptojacking. According to Check Point Software Technologies, 37% of the world’s websites suffer such attacks every year.
How to protect yourself
Attackers use CPU power, as not all PCs have video cards. A user may notice that a certain website is heavily loading the computer. To check a hunch, you need to go to the browser’s Task Manager by pressing Shift+ESC.
If the resource is “infected”, the system will show this. For example, one of the tabs consumes 100 MB of memory and 100% of CPU time. At the same time, loading other pages takes 20 MB of memory and 20% of the PC’s CPU resource.
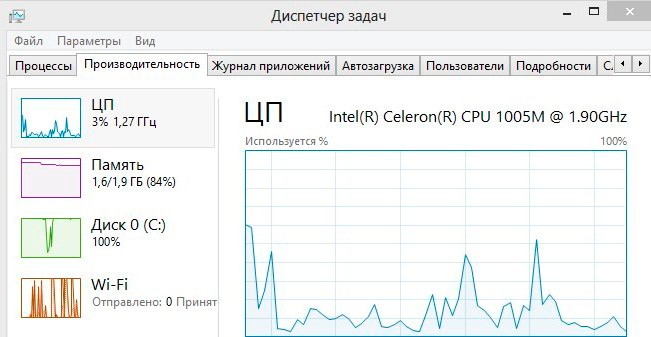
You may also notice overheating of the computer (noise from the coolers increases) when visiting certain sites. The cause of this “hang” may be the work of a hidden miner embedded in the code of the page. The table contains ways to fix the problem.
| Solution | How to perform |
|---|---|
| Edit the hosts file – manually add known domain addresses to the blocking list. |
|
| Use browser mining blocker utilities (for example, Anti-WebMiner). |
|
| Disable JavaScript in the browser. This method is not suitable for all sites. Some platforms need JavaScript to work properly. |
|
| Install the AdBlock or UBlock ad blocker. |
|
The latest versions of the Chrome browser have built-in protection against hidden mining. The user does not need to perform any actions. When visiting pages that consume a suspiciously high amount of resources, the system will automatically put the PC into power saving mode.
However, if the user is working on a powerful device with a multi-core processor, and the scammers have set the CPU load limitation to 30-50%, it may be difficult to determine the unauthorized waste of resources. To prevent “infection”, it is worth installing a good antivirus and running regular system scans.
Avtor: Saifedean Ammous, strokovnjak za ekonomijo kriptovalut.














