
Offline storage has a large market share and is considered the best security solution for all users of digital assets. Manufacturers offer devices with different prices and characteristics. To navigate the choice, you need to consider the rating of hardware wallets for cryptocurrency. But before comparing models, you should understand their properties, consider how they work.
Features of hardware storage
Such wallets are small computer devices, similar to flash drives. They are used for long-term saving of coins. On the market, services are available both for storing only one coin, and multicurrency.
Hardware bitcoin wallets were originally designed to store BTC, but after improvements, they can accommodate other cryptocurrencies.
The device is not connected to the Internet, so such a wallet is called a cold wallet. Its advantages:
- Not susceptible to hacking through computer viruses.
- The security of the storage is ensured by the fact that the private key is on a special chip. It can not be transferred from the wallet in the form of an open text. Even if it is stolen, an intruder has no access to the pin code, and in case of hacking after 3 erroneous attempts it is blocked and can be restored only by entering a cid-phrase.
- No one but the owner knows the size of the asset.
- Having an open source feature that allows you to verify transactions on the device.
You cannot transfer coins from a hardware wallet without knowing the secret pin code. Spyware or Trojans cannot record what happens on the device.
What is a private key
When a user registers an account with the service, they are provided with two pairs of keys: public and private. They are used to generate the address and sign transactions that confirm the ownership of coins. The password is a set of characters that allows access to the account. If it is obtained by someone else, the owner will lose his savings. It can only be recovered using a mnemonic phrase.
5020 $
bonus for new users!
ByBit provides convenient and safe conditions for cryptocurrency trading, offers low commissions, high level of liquidity and modern tools for market analysis. It supports spot and leveraged trading, and helps beginners and professional traders with an intuitive interface and tutorials.
Earn a 100 $ bonus
for new users!
The largest crypto exchange where you can quickly and safely start your journey in the world of cryptocurrencies. The platform offers hundreds of popular assets, low commissions and advanced tools for trading and investing. Easy registration, high speed of transactions and reliable protection of funds make Binance a great choice for traders of any level!
The digital signatures and private key required for payments are generated through the device. It is important to write down the initial word (recovery phrase) on a piece of paper and keep it in a safe place.

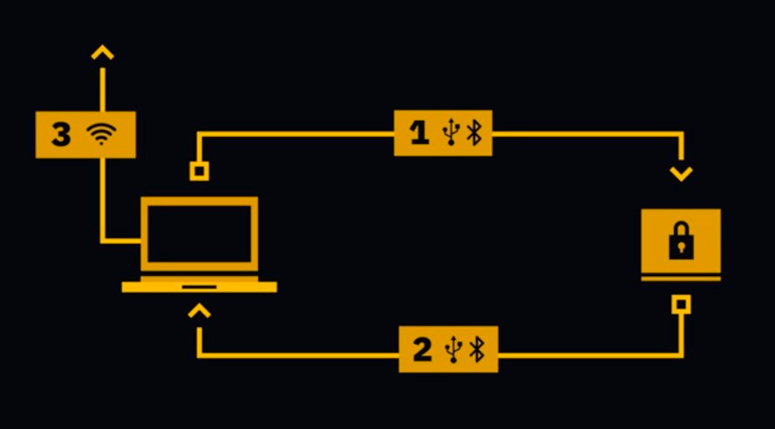
How hardware wallets work
To receive coins, you need to generate an address. The process will start in the background, then the identifier is displayed. It is passed to the sender.
If coins need to be sent, the app creates a raw transaction waiting for approval. The unsigned transaction is sent to the hardware cryptocurrency wallet, where it is confirmed with a password. The signature is then returned to the computer, and the transfer is broadcast on the network.
The private key is stored in the device and is not visible to the PC it is used with. This provides security. If the vault breaks, the owner can apply a mnemonic phrase in the form of a 12 or 24 word entry.
Security
Since the introduction of the first hardware crypto wallet for Bitcoin, there have been no reports of hacks or funds disappearing. Hypothetically possible risks are described below:
- Poor software implementation of the random number generator (RNG), which is used to create cryptographic keys for encrypted data transmission. Attackers can crack the keys created by an insecure sensor.
- Bugs in the software itself lead to the disclosure of sensitive information to third parties.
- Introduction of backdoors (malware) during the production or delivery phase.
Limitations
Hardware vaults lack the flexibility of online applications because you have to carry the device with you for every transaction, and connect it to a desktop PC. They are not free and require an investment. If you lose your wallet, PIN or initial recovery password – you won’t be able to access the cryptocurrency.
Sizes
Standalone wallets come in different sizes. Some are 10 centimeters long, others look like flash drives. They are convenient for storage and transportation. Modern models are similar to mini-computers. Individual types are equipped with a touch screen, one or more buttons for convenient operation.

Differences from other type of storage
To use a hardware wallet for cryptocurrency, you need to connect it to a computer, enter a pin code, a passphrase. Carrying out operations is possible only when the device is active. It does not require the installation of additional programs.
Unlike hot, cold wallets store private keys not on the server, but on a special chip of the device. Only the owner has access.
Standalone storage is more difficult to hack, as it is not easy to gain physical access to it. If the device ends up in the hands of an attacker, he will need to enter a pin code and a mnemonic phrase that are known only to the owner. Hot cryptocurrency wallets have inherent vulnerabilities. Although their databases are safe, there have been cases of hacker attacks on such applications and programs, after which users lost assets.
The cost of individual models reaches up to 250 dollars. However, you can choose to buy a cryptocurrency wallet or create a digital vault without investment. Most of the software is free, provided either by third parties or by the cryptocurrency developers themselves.
Ledger
The company is best known for two types of wallets. Leder Nano S is the first model. It has a secure operating system BOLOS, supports 1800 cryptocurrencies and various tokens.
The Nano X version is more popular. This is the second generation of hardware vaults. It is easy to work with, as navigation is done with buttons (left-right), pressing both at the same time acts as “Enter” to confirm transactions.
Security is provided by its own operating system. Personal keys are isolated on a secure chip. A PIN code is required for access. Transactions and changes made to settings are confirmed by pressing physical buttons. The recovery phrase consists of 24 words. This makes it difficult to compromise the device.
The features of the Ledger Nano X are summarized in the table.
| Pros | Minuses |
|---|---|
| Over 1800 coins, tokens. | Expensive. The price on the official website is €140 (August 2021). |
| Supports major operating systems. | Bluetooth is only compatible with the mobile app, not with desktop. |
| Private keys are inside the embedded chip. | |
| Stores up to 100 apps. | |
| Availability of secure Bluetooth. |
Trezor
Developed by the Czech manufacturer SatoshiLabs. Two models are distributed. Trezor One was released in 2011. It has a deterministic structure, which means that it can store an unlimited number of keys (BIP 0032/BIP 0044). It has fewer features compared to the next version.
Trezor Model T is open source. It can be checked by users for vulnerabilities. It controls private keys. This hardware cryptocurrency wallet works with MyEtherWallet, Exodus, Nano Wallet, Electrum, AdaLite, and MyCrypto services.

The security of cold storage is provided by:
- Firmware verification.
- Mnemonic phrase.
- Ultrasonic seal.
In addition to a PIN code with a length of 4 to 9 digits, encryption passwords can be created to prevent unauthorized access.
The features of Trezor T are shown in the table.
| Pros | Minuses |
|---|---|
| High security. | The need to install additional software to work with certain cryptocurrencies. |
| Compatibility with many services. | Expensive. The price is 159 €. |
| Regular firmware updates. | |
| Support for over 1500 coins and tokens. | |
| Open source code. | |
| Portability. | |
| Password manager offered. |
KeepKey
A development from ShapeShift, a digital asset exchange company. You can connect KeepKey to ShapeShift and easily sell, buy, exchange coins. The device is made with a large display, convenient to use. Selected software wallets such as MEW Ethereum (web version) as well as DeFi platforms allow KeepKey integration.
For security, it serves as:
- Private key. It is stored directly on the KeepKey.
- Pin code. Personal identification number prevents unauthorized users from viewing balances or conducting transactions.
- Backup copy of the passphrase. It is created when setting up the device.
- Passphrase. You can set an additional word to the recovery password.
The features of KeepKey are summarized in the table below.
| Pros | Cons |
|---|---|
| LED display simplifies operation. | Need to download additional software to interact with applications. |
| Supports 40 leading cryptocurrencies. | Large size. |
| Price is only 49 euros. | Does not store history. |
CoolWallet
A development of the Taiwanese hardware wallet manufacturer CoolBit X. Represents a physical card about the same size as a credit card. It is flexible and temperature resistant. The card has a secure chip connected to a mobile app on an Android or iOS device.
CollWallet, CollWallet Pro, and CollWallet S vault versions are available to customers. The last model listed above was released in 2018. It has more features compared to the previous versions.
The security measures include:
- Encrypted Bluetooth for fast and secure transfer of funds.
- SE microchip for storing secret keys.
- Multiple confirmations.
- Self-setting security level.
- Ability to make a copy, as well as restore access to the wallet.
| Pros | Minuses |
|---|---|
| Connects to decentralized exchanges (DEX). | Suitable for experienced traders. |
| Wireless. | Does not support all popular cryptocurrencies. |
| Has a portable form. | |
| Provides easy setup and operation. | |
| Two-factor authentication is provided. | |
| Waterproof, heat-resistant, flexible. | |
| 37 types of coins. | |
| Staking capability for assets that are on the wallet. | |
| Support for Bitcoin, Litecoin, Ethereum, Ripple, Cosmos, Stellar, Tron, Polkadot, Binance Coin, USDT and all ERC-20 tokens. Tezos, Cardano and other coins are planned to be connected. |
Cobo Vault
Developed by blockchain expert Lixin Liu offers premium security features:
- Open source.
- No wireless connections.
- Water-resistant, shock-resistant military-grade case.
- Rechargeable removable battery.
- 4-inch touchscreen with fingerprint sensor.

Security features include:
- Multi-character password.
- QR code communication.
- Open source software.
- Firmware update via SD card.
- Recovery phrase from 12 to 24 words.
- Increased lockout period.
- Self-destruct function.
- Encrypted chip integrating BIP32, 39, 44 protocols.
| Pros | Minuses |
|---|---|
| Open source code. | Difficult to use. |
| Large display, simplifies keyboard operation. | High price. |
| Extended blocking period and self-destruct functions prevent physical intrusions such as brute force attacks. | |
| Supports over 40 blockchains and 180 tokens. | |
| Combination of several security features aimed at keeping private keys private. |
BitLox
An advanced, fully secured digital currency wallet designed to keep bitcoin transactions anonymous. It has the following characteristics:
- 4mm thick and weighs 25g.
- Backup.
- Restore with cid-phrase of 12, 18, 24 words.
- Can be charged with a USB cable.
- QR code scanning for transactions.
- Multiple language support.
- Water and shock resistant.

BitLox customers are offered 3 models with the following differences:
- BitLox Advanced. Coated with aerospace alloy, it allows you to store up to 100 different wallets with unlimited addresses.
- BitLox Ultimate. Unusual design with a titanium case.
- BitLox Extreme. High-performance version of the storage.
BitLox complies with BIP32, BIP39 protocols, which makes it easy to implement mnemonic code. It is hierarchically deterministic. In hidden mode, it can only be accessed with a 4-digit pin code and password. The user-configurable security levels are as follows:
- Standard. Automatically generates a 4- or 8-digit PIN, and a 12-word mnemonic phrase.
- Advanced. You can create your own 60-character PIN, an 18-word backup. There is an additional function “Device tamper protection”.
- Expert. Has an advanced mnemonics of 24 words, as well as a PIN code.
You need to create a pin code for each vault, regardless of the choice of protection mode.
The features of BitLox are presented in the table.
| Pros | Minuses |
|---|---|
| High degree of protection. | High cost – $148-$299. |
| Backup. | Uncomfortable for a beginner. |
| Open source code. | |
| Several languages. | |
| Effective stylish package. | |
| Sturdy metal case. | |
| Supports Tor browser. |
BitBox
A development of Swiss hardware manufacturer Shift Cryptosecurity. The company’s lineup includes BitBox, BitBox01, BitBox02 models. The latter has two versions: the standard one supports bitcoin, ether, lightcoin addresses, and the other is designed only for bitcoin storage.

BitBox02 has a backup card. It has a touch button, an indicator to confirm transactions, and a random number generator.
Security is provided by:
- Enabling two-factor authentication.
- Manual confirmation of transfers.
- Backup and restore.
- Two-chip architecture.
- Official BitBox firmware to protect against threats posed by any third-party code.
- Encrypted USB communication.
- Password protection. Device automatically erases history and reboots after 15 failed login attempts. At the same time, there is protection against password brute force attacks.
| Pros | Cons |
|---|---|
| Emphasis on reliability. | Limited range of coins and tokens. |
| Simplicity of customization. | No screen. |
| Backup, availability of Micro SD. | High price – €119 (as of August 2021). |
Which hardware wallet for cryptocurrency to choose
On the market, customers are offered a wide range of devices for cold storage of digital assets. The choice of a suitable cryptocurrency wallet depends on the tasks set by the future owner. The user can be guided by such characteristics:
- Support of the required types of cryptocurrencies.
- Security options – the presence of two-factor authentication, multiple signature function and others.
- Reliability of the manufacturer. New companies do not yet have authority in the market.
- Openness of the code.
- Ease of use.
- Ability to create a backup copy.
- Attractive design.
- Commissions for services.
- List of provided languages.
- Feedback from other users.
- Availability of wireless network (Bluetooth or NFC).
Where to buy a wallet
Buy hardware storages should be purchased only from official manufacturers and distributors. So you can be sure of the originality of the product.
The features of purchasing autonomous wallets are presented in the table below.
| Supplier | Pros | Minuses |
|---|---|---|
| Manufacturer | Low price. | Significant delivery time. |
| Guarantee of originality. | In many cases there is no technical support in Russian. | |
| Expenses for shipping. | ||
| Official distributor | Fast delivery. | High price. |
| There is support in Russian. | ||
| Replacement without costs in case of malfunction. |
Potential vulnerabilities
Autonomous storage is characterized by reliability, but has hidden vulnerabilities. The main ones are associated with the actions of hackers, unscrupulous suppliers, viruses.
Hacking
Cryptocurrency owners prefer hardware wallets to software wallets because of increased reliability. They offer protection against hacking through a PIN code, which after 3 incorrect attempts is blocked and requires you to enter a seed-phrase. Therefore, it is virtually impossible to hack into such a vault.
Fraudulent vendors
An unscrupulous distributor can counterfeit the device before sending it to the buyer. To protect the authenticity, official manufacturers use a holographic sticker. Its integrity shows that it has not been opened.
You can not use an already configured hardware cryptocurrency wallet. The owner must independently enter the pin code, password, copy the cid-phrase, make a backup copy.
When buying a hardware wallet, it is necessary to make sure that the protective seal is intact.
Compromised cid-phrase
A cryptocurrency wallet must generate a recovery passphrase when set up by the user. It cannot be obtained in advance or with the device.
If the phrase is compromised by a hacker, the hacker will recover the vault and the owner will lose coins.

Viruses
Hardware wallets offer an extra layer of protection against various cyberattacks, malware intrusions on any personal computer. You need to keep your secret key and a copy of it in safe, secure places.
Regardless of the type of storage, there is malware that allows you to change the recipient’s address to an identifier belonging to the attacker. Multi-factor verification will avoid the problem.
Evil maid
This is an attack that physically attacks a device that has been left unattended by the owner. Since the case can be disassembled, it is necessary to establish whether it has been tampered with. Special holograms or epoxy are used for this purpose.
If the owner discovered that the device was damaged, it is necessary to enter a mnemonic recovery phrase to send coins to a new vault with a different password.
5-dollar attack
The name of the vulnerability is associated with physically threatening the owner of an offline vault with a wrench equivalent to the value of $5.
Some cryptocurrency wallets have additional layers of protection added after the PIN. The user can customize the service so that different passwords display separate accounts. For example, do not disclose the amount contained in the account, but show only a small part of the coins.
How to make a hardware wallet for cryptocurrency from a USB flash drive
This method can be used under long-term storage. To create a cold wallet for cryptocurrency on a flash drive is not difficult. It is necessary to consider the process with the Electrum application step by step:
- Prepare a USB drive with a size of 8 GB or more.
- Download the open source operating system Tails.
- Download the Electrum application to your computer. It takes up a small amount of memory.
- Install the OS on a flash card. This is recommended for maximum reliability.
- Download the application to the operating system on a USB flash drive.
It is recommended to use this flash drive only as a physical cryptocurrency wallet without downloading other programs and files.
- Select the type of protection: standard, two-factor, multitasking.
- Disconnect the computer from the Internet.
- Conduct further installation offline.
- Take out the flash drive.
- Reboot the PC.
- Check the operation of the operating system without the Internet.
- Connect the USB to the computer.
- Go to the flash drive folder and open the service installation program. It will not be able to connect to the Bitcoin network, but it will create a new storage.
- Conduct a standard installation. The new application will be placed in the OS of the USB drive.
- Create a strong password.
- Record and then duplicate the generated 12-word recovery passphrase.
After setting the password and writing the seed phrase, the new physical wallet for cryptocurrencies and BTC on the flash drive is ready to go. Now you can accept and send coins.
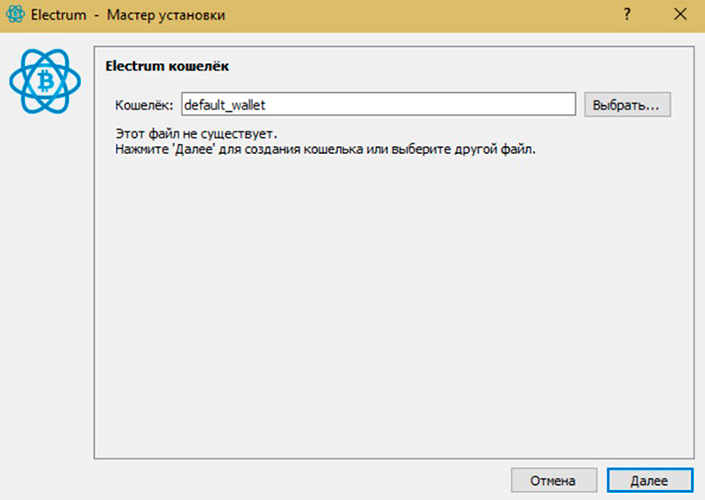
If everything is done correctly, a flash drive for storing cryptocurrency will not be inferior to hardware devices in terms of reliability. If you install the application without a boot system, it will have a lower level of security.
Summary
With offline storage, digital assets are under the control of the user. They are protected through pin code, password, recovery phrase.
When choosing a wallet, you should consider the price, list of supported coins, interaction with digital applications and other features.
Regardless of the choice of storage should:
- Make copies of the cid-phrase and place it in a safe place: it serves to recover keys in case of theft, breakage, loss. You should keep a copy in a secure location, preferably not in the cloud or on your computer’s disk.
- Verify addresses before confirming transactions: although attackers cannot remotely hack the hardware vaults that sign bitcoin transactions, they use other methods. For example, cryptocurrency malware changes wallet addresses copied by the user to the clipboard.
- Only buy the device from an official vendor or manufacturer.
- Remember that the seed phrase is generated by the storage itself and should not be received when it is delivered.
Frequently Asked Questions
🙋♂️ What happens if I lose my hardware storage?
You can restore accounts to a new device using the seed-phrase.
❓ Will an arc hardware cryptocurrency wallet be needed if new cryptocurrencies emerge?
A newly released digital coin is rarely directly backed by an offline vault. However, most providers like Ledger or Trezor are constantly adding new cryptoassets.
💻 Can all cryptocurrencies be restored with an offline vault backup?
Often services support more than one coin, but create only one backup. It is enough to restore all digital assets, as it contains the initial value of the private keys created during setup.
💵 How to manage coins using a physical wallet?
When sending assets, the owner has to confirm it on the screen. The transaction is then signed with the private key.
📱 Is a standalone device compatible with a software device?
Digital apps keep cryptocurrency safe by allowing integration with a physical wallet.
🤔 Can coins be accessed if you forget the pin code?
In such a situation, the device will be locked. The only way to restore the accounts is through a seed phrase.
❔ Is it safe to turn on Bluetooth?
It does not pose any serious threats because the private keys are inside the device. The Bluetooth connection is encrypted. Even if it can be hacked, you will need a PIN to access it.
Misspelled text? Highlight it with your mouse and press Ctrl + Enter
Author: Saifedean Ammous, an expert in cryptocurrency economics.














