One of the main fiat problems Bitcoin was created to solve is the lack of privacy of user information. The unknown developer of the cryptocurrency payment system sought to make Bitcoin anonymous. For this purpose, the creator used decentralized information storage technology and other methods of increasing privacy. However, the absolute anonymity of Bitcoin could not be achieved. In this regard, it is useful for users of cryptocurrency to know how to keep personal information confidential.
The principle of bitcoin transactions work
To achieve consensus (a single point of view on the cryptocurrency chain) in the Bitcoin blockchain, miners use the Proof-of-Work (PoW) algorithm. The mechanism is based on the use of computing power of computer hardware. It performs 2 tasks:
- Finding the hasj (abbreviated identifier of an array of encrypted information) of transactions and network blocks.
- Checking the validity (validity) of the updated version of the system and synchronizing the miners copies of the chain if the obtained values are correct.
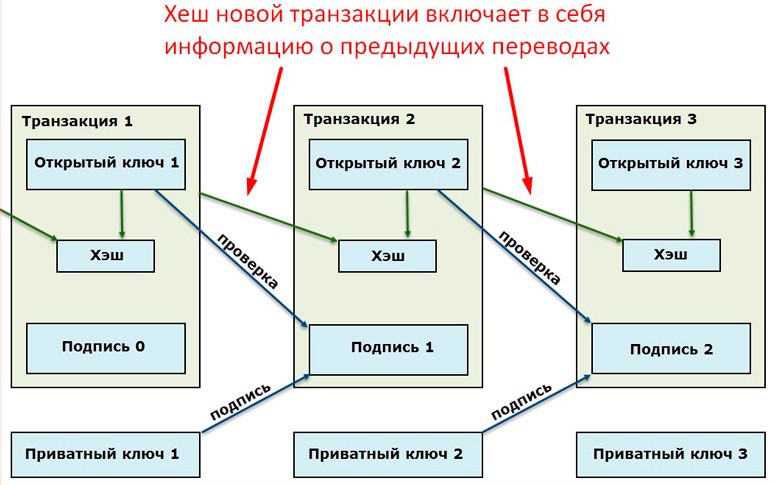
Bitcoin transactions are sequentially included in blocks. Hierarchy is needed to build the correct structure of the cryptocurrency chain. Bitcoin transactions reference each other for the same reason. For example, a random user sends 10 BTC to a fellow user. First, miners must check where these funds came from in the wallet of the initiator of the transaction, and then – where they should be transferred to.
Bitcoin network participants use a digital signature to confirm transactions. It is generated on the basis of a private key assigned to the wallet of the initiator of the transfer.
In each new block, the beginning of the list of Bitcoin transactions is the miner’s reward for creating a link in the digital chain. Such transactions are assigned the coinbase program property, which can have any content. However, in the following Bitcoin transactions, it is replaced by a scriptSig parameter that includes the public cryptocurrency key of the recipient of the previous transaction.
5020 $
bonus for nye brukere!
ByBit gir praktiske og trygge forhold for handel med kryptovaluta, tilbyr lave provisjoner, høyt likviditetsnivå og moderne verktøy for markedsanalyse. Den støtter spot- og leveraged trading, og hjelper nybegynnere og profesjonelle tradere med et intuitivt grensesnitt og opplæringsprogrammer.
Tjen 100 $ i bonus
for nye brukere!
Den største kryptobørsen hvor du raskt og trygt kan starte reisen din i kryptovalutaverdenen. Plattformen tilbyr hundrevis av populære aktiva, lave provisjoner og avanserte verktøy for handel og investering. Enkel registrering, høy transaksjonshastighet og pålitelig beskyttelse av midler gjør Binance til et godt valg for tradere på alle nivåer!
What makes bitcoin anonymous
The blockchain keeps user data private. The anonymity of Bitcoin is conditioned by such features of the network:
- No binding of cryptocurrency addresses (numbers) to users. To generate a new vault, participants of the Bitcoin system do not need to specify personal information. Also, they can create wallets in any number when needed.
- There is no binding of bitcoin transactions to their initiators. BTC holders don’t need to provide personal information to make a cryptocurrency transfer either.
- Randomization of the selection ofnodes(nodes) for processing transactions. Bitcoin transaction data is relayed by miners within the network. Although mining nodes communicate with each other via IP addresses, they cannot be sure that they are receiving transfers from their initiators for processing.
How anonymity is revealed
The privacy of Bitcoin network users can be compromised. Because of this, the cryptocurrency community considers the Bitcoin system to be a pseudo-anonymous coin. There are 5 ways to identify the identity of a BTC sender or receiver:
- Time.
- Source of funds.
- Transaction graph.
- Clustering.
- Heuristics.
Time
Bitcoin is a transparent digital blockchain. Users are free to take public information from the blockchain if needed. It is easier to do this through crypto network monitoring services.
Using public information, it is possible to determine the territory where the owner of the selected wallet resides by analyzing it. To do this, you need to:
- Select a bitcoin transaction.
- Copy the hash of the transfer.
- Find the sender’s or recipient’s wallet (depending on the purpose) by the identifier of the bitcoin transaction through the cryptocurrency network monitoring service.
- Use the obtained wallet address in an advanced blockchain browser like oxt.me.
- Determine the period of the lowest activity of the wallet (in the monitoring service it is specified by UTC).
After the fifth step, you will need to add some time to the found period. For example, if the average period of the lowest activity was from 17:00 to 22:00 UTC, you should move it by 8 hours upwards. Then you will get the interval from 01:00 to 06:00 GMT+8. The owner of the selected wallet most likely lives in this time zone.
Source of funds
In digital networks there is a concept of “transaction inputs”. They are a kind of history from where the cryptocurrency comes to a new address – UTXO (source of funds). Transaction inputs allow you to bypass the anonymity of BTC.
Because bitcoin transfers are stacked in a sequential chain, the UTXO is not the sender’s wallet address or the hash of the transaction itself. Technically, the source of funds is the unspent output (recipient) of the previous transfer.
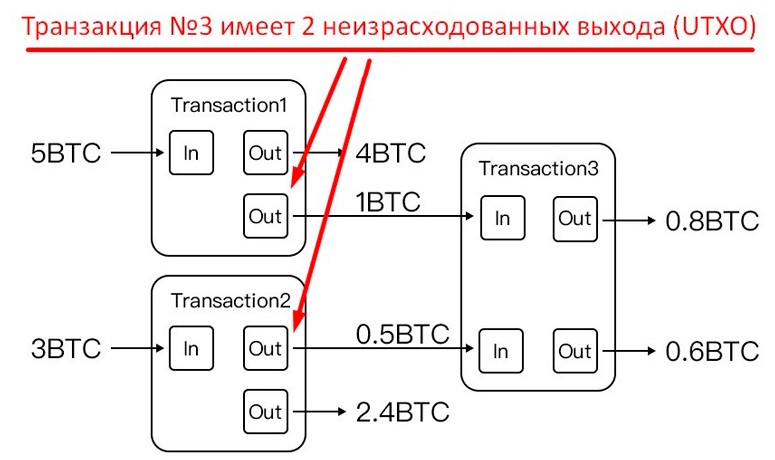
You can determine UTXO by using advanced crypto network monitoring services. They show the entire list of inputs and outputs of Bitcoin transactions and how transfers are actually made. With this information, it is easy to know the amount of bitcoins in the wallet of the monitored user.
Transaction graph
Thanks to UTXO, bitcoin transfers are collected into a chain. In the community of digital asset users, it is called the BTC transaction graph. It can be used to track the transfer of cryptocurrency from Bitcoin wallet A to storage B. At the same time, the depth of use of the graph is not limited. Participants of the Bitcoin blockchain can track the full history of cryptocurrency transfer before and after a particular transaction.
The owners of some addresses are known to the public. These are mostly the vault numbers of popular personalities or large companies. When bitcoins arrive at a known address, it will be possible to tell exactly who the cryptocurrency belongs to.
Clustering
Bitcoin transfers can have multiple sources. These often include change addresses. Such numbers are automatically generated by the service where the user created a bitcoin wallet. They are needed to transfer change back to the account of the initiator of the BTC transaction.
In the Bitcoin blockchain, this process happens automatically and is often unnoticeable to its participants.
From a technical point of view, the total number of coins in the vault is one “bill”. It is not possible to send only a portion of it. To conduct a bitcoin transaction, you need to send a whole “bill”. The remainder of the amount is returned as change. This principle is similar to paying for goods in a store.
Bitcoin change addresses and other UTXOs can be collected into groups. This process is called clustering. An analyst gathers information about different sources of funds to determine their involvement in funding a particular wallet. By collecting such a cluster, it can be assumed that they belong to a common owner. At the same time, revealing the owner of one address will lead to de-anonymization of the whole cluster.
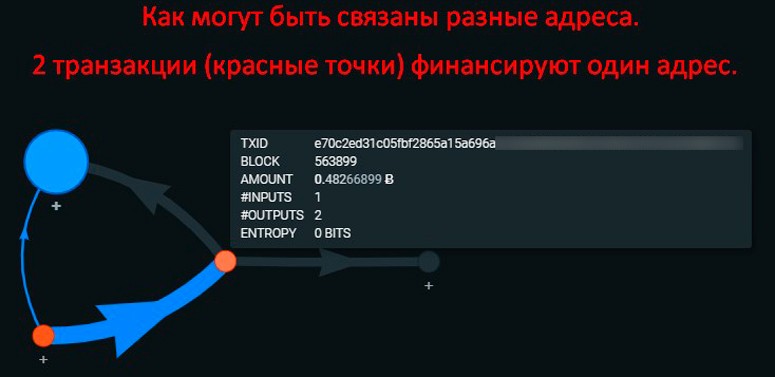
Heuristics
Time, UTXO, Bitcoin transaction graph and clusters together allow you to associate a single owner with a group of addresses. All of this information is called “heuristic data”. They have the potential to reduce the anonymity of bitcoin. However, sensitive information can be protected.
How to keep bitcoin anonymity
In 2021, there were 3 popular methods to increase privacy:
- TOR. Browsers based on The Onion Router technology use multi-level encryption of the connection with 3 keys to connect to the internet. These are generated randomly as the signal passes through proxy servers (intermediate links between the user and the network). Tor allows you to hide your IP address and any other information.
- Mixers. With the help of such software, it is possible to anonymize the initiator of the following bitcoin transactions. Mixers collect users’ cryptocurrency and carefully “mix” it by distilling digital assets to different addresses. As a result, network participants receive the invested amount back, but from different senders and in installments.
- Special wallets. There are opaque vaults through which you can anonymously send cryptocurrency. They close access to information about the addresses and bitcoin transactions of clients. In this case, the owners of the service have several crypto wallets. After receiving coins on one, they send a similar amount from the others. As a result, it is almost impossible to link these transactions.
How to buy BTC anonymously
Attackers can establish the identity of the wallet owner by several methods. For this reason, many investors and traders try to buy bitcoins anonymously. There are 3 main ways:
Lightning Network
LN is a layer 2 protocol or technology for creating payment channels on top of the main blockchain of the BTC coin. Lightning Network was created in 2015 by the development team of the cryptocurrency organization Bitcoin Core.
LN technology is able to keep bitcoin anonymous for 3 reasons:
- BTC transactions from payment channels do not have to be included in the blocks of the Bitcoin public registry.
- TOR technology is used for anonymization.
- There is no way to cluster Lightning transactions.
Other methods
To preserve the confidentiality of personal data, you can buy BTC coins directly. First, you need to find a seller and agree on the terms of the transaction. It is recommended to insist on a deal at a personal meeting. This approach will reduce the risk of fraud.
In a direct transaction, the user receives coins by regular transfer from the sender. The very fact of purchase is not recorded on the Internet.
Another way to maintain confidentiality is to use the services of services on the darknet. However, such resources operate semi-legally or illegally. Also, services from the shadow Internet charge high fees for their services. For example, a monthly subscription to use the semi-legal resource Helix costs 0.01 BTC ($464 at the exchange rate as of December 15, 2021), and you will have to pay a 2.5% commission on each transaction.
The policy of exchanges on the anonymity of Bitcoin
Most popular cryptocurrency trading platforms require customers to verify their identity with a passport or other document. This is due to pressure from the financial regulators of the countries in whose territory the exchanges operate. For this reason, trading platforms have a negative attitude towards virtual assets that preserve the complete privacy of users.
Anonymous cryptocurrency
Bytecoin is considered the progenitor of such digital assets. The project was developed in 2012 based on the CryptoNote encryption algorithm. This mechanism ensured the confidentiality of user data. In 2021, there were more than 5 other anonymous digital projects.
| Mynt | Kort beskrivelse |
|---|---|
| Monero | The project was created in 2014 as an offshoot of the main chain Bytecoin. Previously, the cryptocurrency was called BitMonero, but was renamed a few days after the release. The blockchain uses the CryptoNote encryption algorithm. |
| Zcash | The project was officially launched in 2016. The main developer took inspiration from Bitcoin, but tried to make Zcash anonymous. One of the advisors of the project was Vitalik Buterin, the creator of Ethereum. The zk-SNARK protocol is used to anonymize Zcash. |
| Dash | The project was founded in 2014 by Evan Duffield. It too was inspired by the Bitcoin system, but used built-in mixers in Dash to increase anonymity. |
| Verge | The project appeared in 2014 and became an offshoot of the main Bitcoin blockchain. The Verge network uses TOR and I2P (“invisible internet”) technologies to obfuscate IP addresses and transactions. |
| PIVX | The project was created in 2016. The PIVX network has become an offshoot of the DASH blockchain. The coin is considered even more anonymous compared to its parent digital currency. PIVX utilizes the robust Zerocoin hashing algorithm. |
Sammendrag
Despite the lack of binding transaction and wallet data to users, the Bitcoin network is pseudo-anonymous. The confidentiality of information can be compromised using heuristics techniques. The sources of funds – the unspent outputs of previous transactions – UTXOs play a major role in this.
To preserve the anonymity of bitcoin will help:
- The Onion Router. Technology of multi-level encryption of the Internet connection.
- Mixers. Software for “mixing” UTXO.
- Opaque wallets. Vaults that block access to users’ personal information.
- Lightning Network technology. The second layer protocol of the Bitcoin system.
Ofte stilte spørsmål
❗ Why do I need consensus when verifying transactions?
With the help of a special algorithm, miners come to a consensus point of view and update their copies of the network. Consensus avoids errors in the blockchain.
✅ Is the anonymity of fiat and Bitcoin different?
Yes, traditional financial services (banks, exchanges) are characterized by centralization and the requirement for customers to provide personal information.
📩 Why do cryptocurrency companies collect clusters of digital addresses?
Sometimes for personal purposes, but often they share the information with law enforcement or other virtual money organizations.
🤫 Who needs anonymity in cryptocurrencies?
More often it is needed by ordinary users of digital networks. However, sometimes cryptocurrencies are used to organize criminal activities – illegal trafficking of weapons, drugs and so on.
❌ Should I use darknet services for anonymization?
No, it is not recommended to turn to such resources. Cryptocurrency on the darknet can be involved in crimes. Then the average user risks becoming an accomplice to the attackers.
En feil i teksten? Marker den med musen og trykk på Ctrl + Kom inn.
Forfatter: Saifedean Ammous, en ekspert på kryptovalutaøkonomi.















