
The main advantages of blockchain are the security of storage and the immutability of data within the network. These are achieved by linking cells into a chain and cryptocrypting them. However, the model of such a connection was born before the realization of the first blockchain network. In the material, readers will learn how the Merkle tree is organized and to what extent it participates in cryptotechnology. We will tell you about the forms of the concept developed over the 30 years since its creation, as well as the main strengths and weaknesses of such a model.
What is a Merkle tree
It is a way of organizing data that helps to easily verify the accuracy and ensure the security of digital information. In Merkle structure, each array is examined, compressed and encrypted. It is assigned a code, which is called a hash. Such values are unique and closely related to the data written in the array.
Who came up with the concept
The development of communication schemes began in the 1950s. At that time, they took the form of an inverted tree. An important stage in the creation of the concept is recognized as 1979, when the American scientist and engineer Ralph Merkle (Ralph Merkle) presented his data linkage structure. The model was named after the author’s surname – Merkle Tree (in English version – Merkle Tree). The concept later became the basis for blockchain technology.
Since the 1990s, the hash tree has been used in the structure of cryptographic protocols, namely as a key element in the generation of digital signatures and authentication of transactions. They were also developed by Ralph Merkle.
Why hash trees are needed
The security of digital information is the main feature of this type of communication. In the 30 years since its introduction, the concept remains relevant. It is successfully applied in various areas of information systems. Internet connections, cryptographic encryption algorithms, and most blockchain technologies are based on it.
Structure
With the development of information capabilities and computers, data has become too much. Large arrays are difficult to process, so it was necessary to reduce their volume. Hash functions were created to compress data.
5020 $
bonuss jauniem lietotājiem!
ByBit nodrošina ērtus un drošus kriptovalūtu tirdzniecības nosacījumus, piedāvā zemas komisijas maksas, augstu likviditātes līmeni un modernus tirgus analīzes rīkus. Tā atbalsta tūlītēju tirdzniecību un tirdzniecību ar sviras finansējumu, kā arī palīdz iesācējiem un profesionāliem tirgotājiem ar intuitīvu saskarni un pamācībām.
Iegūstiet 100 $ bonusu
jauniem lietotājiem!
Lielākā kriptovalūtu birža, kurā varat ātri un droši sākt savu ceļojumu kriptovalūtu pasaulē. Platforma piedāvā simtiem populāru aktīvu, zemas komisijas maksas un progresīvus rīkus tirdzniecībai un investīcijām. Viegla reģistrācija, liels darījumu ātrums un uzticama līdzekļu aizsardzība padara Binance par lielisku izvēli jebkura līmeņa tirgotājiem!
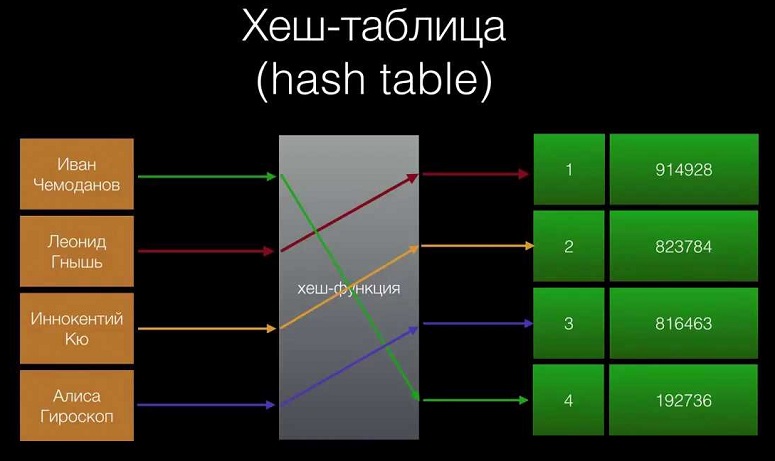
This is an algorithm that uses input digital information (for example, a text string or any binary data), and as a result produces a short version – a hash code. Its length is fixed by a parameter, which helps to make the amount of data compact and more convenient for further work.
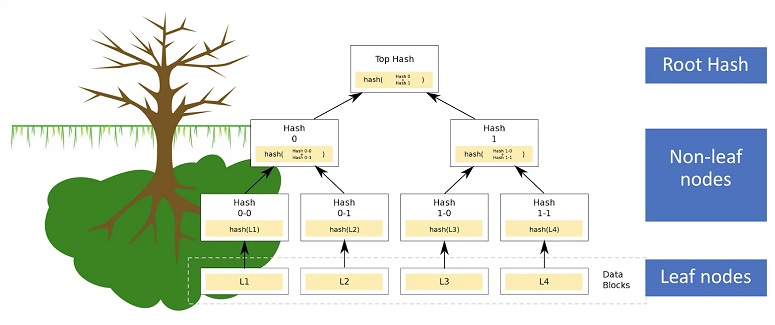
Ralph Merkle proposed a universal scheme for connecting the obtained values. At the top of the structure is the main hash code – the chain identifier. Its other name is Merkle’s root. Each node in the scheme also gets its own hash, and “leaves” correspond to individual blocks.
Darbības princips
First, each array of information is collected into a single block. A “header” of fixed length (hash code) is created for it.
Then the phrases are encoded in pairs, and a new value is calculated for each mapping. The process is repeated for all blocks in the structure – once and until a single root total (the hash of the “tree”) is obtained.
This concept has an important property: the data cannot be tampered with. If this happens, the root in the block will change. First, an updated header will be generated, then the codes of the following cells will be changed along the chain.
The protection against hidden data substitution is called invariance. On the one hand, it guarantees the authenticity of information in blocks. On the other hand, it makes it possible to determine where the data has changed.
Merkle’s scheme is used for transactions, block formation and network construction. In sequential chains, authentication is required for each cell. Merkle Tree, on the other hand, uses only the root. Analyzing each “tree” in its entirety becomes unnecessary. The main value acts as a guarantee of information verification within the structure.
By reducing the time spent on verification, networks become faster.
The classic Merkle concept has a modified version – with several hash functions. This algorithm uses different encryption methods. For example, the most popular encryption type SHA-256 is strengthened with an additional hash function SHA-3, BLAKE2 or others.
There is another variant of the Merkle hash tree, the Merkle Patricia Tree (MPT), which is suitable for finding information within a tree structure. The traditional Merkle Tree is primarily used in authenticating the authenticity of the information recorded in the tree. Structures are also used concurrently – for example, in the Ethereum network.
Analogs
The Merkle communication method is not the only type of data organization. There are dozens of hash trees. Some help to increase the speed of searching for the necessary information. Others sort information according to a selected condition. Trees help to organize data storage and create indexing systems based on certain string elements.
Among the concepts, there are the following types:
- Binary or Binary Tree (Binary Tree). In this method, each node includes no more than two descendants (left and right). The concept is applied to the realization of data structures.
- Binary Search Tree (BST). It is a complicated version of the previous method. In it nodes create conditions for sorting (keys), by which elements are searched. The method also allows you to delete or insert new information.
- AVL-tree. The name is derived from the first letters of the authors’ surnames. They were Soviet scientists Adelson-Velsky and Landis. The scheme developed by them is based on the BST-structure. Here in each node the height is limited. The parameter is used to search and update data in the structure.
- Red-Black Tree. Another balanced is a binary scheme in which the root and leaves are black. Red nodes are composed based on pairs of values of opposite color.
- Prefix and suffix trees. The hashes in these are created by considering the beginning or end of strings. Merkle’s model was an extension of prefix-based communication.
- B-tree. This concept creates keys at each node and also divides the data into multiple blocks. Hash trees organize information in external media with sequential access – such as hard drives.
Impact on the crypto industry
The first blockchains – e.g. Bitcoin, Ethereum networks – are based on the Merkle tree. It creates a chain where data in existing cells cannot be substituted. The functions inherited by the blockchain from the Merkle concept are summarized in the table below.
| Feature | Komentārs |
|---|---|
| Each block contains hash sum of transactions and codes of previous cells. This makes the chains resistant to changes. | |
| When analyzing records, nodes need to compare a small amount of information – for example, only the hash headers of cells. This is especially important in mining, here nodes compete to add new solutions to the blockchain. | |
| Changing information in one cell results in the generation of a new hash sum, including in subsequent elements of the chain. This makes it harder to tamper with or delete transactions. | |
| Storing compressed and encrypted data helps to write faster on the network. However, this speed is not enough in modern blockchains. Sidechain networks are created to solve the problem. | |
| The transaction verification in the algorithm is also based on this model |
How the Merkle tree is applied in blockchain
This structure became the foundation of one of the main crypto processes – mining. According to Merkle’s concept, all transactions are performed and blockchains are created. Users search for hashes and are rewarded in digital currencies. On the action side of the network, the structure provides quick authentication – verification.
Kalnrūpniecība
The first blockchains were created on a proof-of-work system – Proof-of-Work (PoW). To get a hash value, you need to solve a problem using hardware. When the result is found, the block is considered closed and a cryptocurrency reward is paid. The equipment (and the owners of the equipment) are called miners, and the process is called mining of digital assets.
Essentially, transaction data is organized in a block similar to a Merkle tree. The resulting output that closes the cell becomes the root hash.
Blockchains are sequentially linked Merkle trees.
However, there are also Merkle Tree elements in the blockchain linkage. For example, each successive cell uses the end of the previous root. This is how the concept participates in the different stages of the chain.
Verifikācija
Merkle’s tree helps to work with the existing blockchain. It is possible to evaluate the authenticity of the recorded data – in other words, to perform verification. For this purpose, the main values – hash codes of blocks and the root – are checked. If they match, the transactions are recognized as authentic and the next block is attached to the end of the chain.
A more balanced version of the Merkle Patricia Tree (MPT) optimizes the search for information in the blockchain. For this purpose, the algorithm uses keys in the structure. Nodes (nodes) use them to quickly find the desired transaction or information in the tree. In this method, selected hashes are analyzed. It is not necessary to go through each code specified in the block.
In some cases, validation is performed based on the integrity of the transaction data. For example, only the latest root hashes in the network can be evaluated.
Advantages and disadvantages of hash trees
The concept has both strengths and weaknesses. They are listed in the table for comparison.
| Priekšrocības | Trūkumi |
|---|---|
| Data invariance. Hash trees make it difficult to forge information. The root value will signal this. | Costs of creating a block (tree). Mining a hash in a crypto network requires productive hardware. However, the complexity of the search is constantly growing, so computing resources need to be regularly increased. |
| Speed of operation. With Merkle linkage, inferences are made based on hashes and without spending resources to analyze the array. | One-way structure. Protection against data changes in the chain is considered both an advantage and a disadvantage. It is not possible to undo an erroneously created transaction. |
| Space saving. Hash trees reduce block size because they store only the root of the structure. | Lack of guarantee. There may be a small probability of finding the same hash values for different blocks. This is called collision. Therefore, you cannot give a 100% guarantee of reliability. |
| Fast access to data. The concept helps to additionally index transactions. | Size Limitations. Information in a Merkle tree is stored in a compressed form. However, a lot of information is generated, and this slows down the work with it. Therefore, additional optimization methods are required: new encryption algorithms, network hardforks, and more. Such changes help compress data, speed up block mining and increase the volume of cells. |
| Security. Hash trees are built on cryptographic encryption algorithms. This protects networks against attacks and data tampering. | Dependency with structure. The effectiveness of hash trees is related to the proper design and organization of the array. Such a concept is difficult to implement in an existing network with large amounts of information. |
Simplified Fee Verification
Part of data integrity analysis is performed on block headers. Such a scenario is involved in simplified payment verification (SPV). It primarily increases the throughput of crypto and traditional networks.
Instead of fully loading the blockchain (database), a node in the chain requests only the cell headers. This creates a proof (Merkle Proof) that the transaction being verified is included in the blockchain.
Nodes verify transactions in the Merkle scheme and save resources when exchanging data. In other words, the smaller the amount of information in transmission, the faster the proof is performed. SPV makes transactions more efficient and easier on devices with under-performing resources – such as cell phones.
Biežāk uzdotie jautājumi
🔔 What is hashing?
It is the process of gathering information into a block and creating an encrypted code. Mining essentially performs hashing transactions for a payout.
📢 Where else is Merkle’s scheme used?
Repositories have been created using this structure – for example, the GitHub resource. You can find source code for both blockchain products and classic applications and websites.
📌 What is version control?
It is the ability to rebuild within the Merkle structure. For example, if needed, there is an option to load a previous version of the data or select a more appropriate version in the schema.
✨ What are the encoding methods used in the blockchain?
Otherwise they are called hashing or mining algorithms. There are already several dozens of such methods. The most popular ones are SHA-256, Ethash, and Scrypt.
⚡ Can a hash be decrypted?
Simple algorithmic functions can be decoded. However, if cryptocryption was used, it is very difficult to unravel the hash. It would take decades. If a combination of several cryptographic algorithms is used, decoding can take millions of years.
Kļūda tekstā? Izceliet to ar peli un nospiediet Ctrl + Ievadiet
Autors: Saifedean Ammous, kriptovalūtu ekonomikas eksperts.














