
In cryptocurrencies, a private code gives the user access to the assets. Whoever logs into a bitcoin wallet using a private key has full control over the coins stored in the wallet. For this reason, it is important to keep access to your BTC addresses secret. If we compare the cryptoasset system to traditional forms of banking, the public address would be an account number and the private password would be a PIN that allows withdrawals.
What is a bitcoin wallet private key
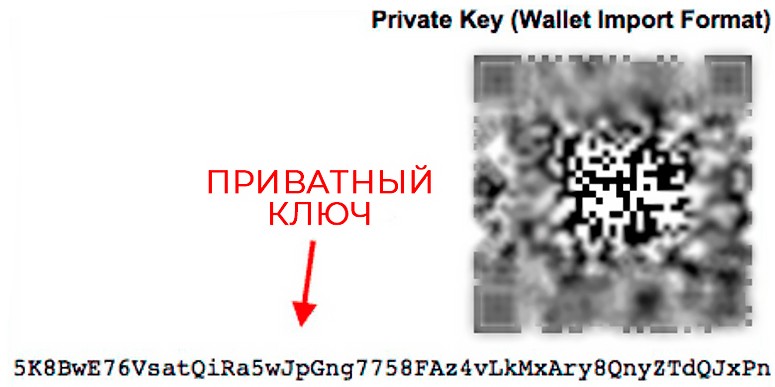
A very long string of numbers and letters jumbled together at random. This is the definition that can be given to the term “Bitcoin wallet private key”. This cryptographic password is mathematically related to the public address.
The concept of private code protection is at the heart of bitcoin, as well as other digital currencies. Since coins and tokens are decentralized (exist on a network without intermediaries), securely maintaining the closed codes is the primary concern of the crypto investor.
If a user loses their PIN, they can easily regain access to their assets through the bank. The loss of the combination of letters and numbers that allow the disposal of cryptocurrencies means that the funds will no longer be in circulation.
There are many known cases where crypto investors have lost their coins due to their lack of access to bitcoin wallets. James Howells, an IT professional from Wales, accidentally threw away a hard drive that held the codes and passwords for 7,500 BTC.
What it’s for
Because cryptocurrencies are virtual assets that exist on the blockchain, wallets are not created to store coins and tokens, but to interact with the network more easily. The software generates and keeps private and public bitcoin address keys secure. This is how users gain access to their cryptocurrencies that are in the blockchain.
5020 $
bonus for new users!
ByBit provides convenient and safe conditions for cryptocurrency trading, offers low commissions, high level of liquidity and modern tools for market analysis. It supports spot and leveraged trading, and helps beginners and professional traders with an intuitive interface and tutorials.
Earn a 100 $ bonus
for new users!
The largest crypto exchange where you can quickly and safely start your journey in the world of cryptocurrencies. The platform offers hundreds of popular assets, low commissions and advanced tools for trading and investing. Easy registration, high speed of transactions and reliable protection of funds make Binance a great choice for traders of any level!
For example, “A” wants to buy a latte at a coffee shop. The price of the drink is 0.0005 BTC. Prior to the transaction, “A’s” funds are stored in a cryptocurrency wallet. To pay for the drink, the user needs to provide the Bitcoin network with his address information as well as a digital signature. This is how BTC settlements are made.
A digital signature is a secure way to publicly verify ownership of a private code without having to disclose its contents. It is a one-time password that is generated for each new transaction.
If “A” is the only person who knows their private keys to BTC wallets, only they can create the digital signatures needed to spend funds from the cryptocurrency.
For example, “A” has 1 BTC. The user creates a transaction for 0.0005 BTC to pay for a drink. Along with the transaction, a unique digital signature is transmitted to the network. The transaction is broadcast on the Bitcoin blockchain and validated by nodes. That 0.0005 BTC goes to a Bitcoin address belonging to the coffee shop. However, no one else can spend the 0.9995 BTC remaining on wallet “A”.
If the user or a third party tries to apply the same digital signature for a second transaction, the Bitcoin nodes will reject the transaction. A new code will be required for the second transaction.
What it looks like
There are 3 common formats in which the same private key can be expressed:
| System | Description | Type |
|---|---|---|
| Hexadecimal | A record that uses only the numbers 0-9 and the letters A-F. Codes written in binary or decimal format can be easily converted to hexadecimal. | DA46B559F21B3E955BB1925C964AC5C3 B3D72FE1BF37476A104B0E7396027B65 |
| Wallet Import Format (WIF) | Often used because: They are much shorter. This helps reduce copy and paste errors. They use base58Check encoding (where 58 different letters and numbers are used). Private keys for WIF always start with “5” and compressed keys always start with “K” or “L”. | 5KUR9tz4iDTpW2xQkNvJDKyGH YWT9q8LriTLH29Tv8Thiyqvy9A |
| Compressed WIF | L4Y1cGSsNv1Nf9dZpTkEyQjLU 24zRyRQeRyE5i4MoVvrjrrr15Koy |
The compressed format, as shown in the example, is one byte longer than WIF. It is so called because it instructs software to extract short publicly available code from it. WIF requires the cryptocurrency wallet software to be able to retrieve an uncompressed public alphanumeric password.
Differences from a public address
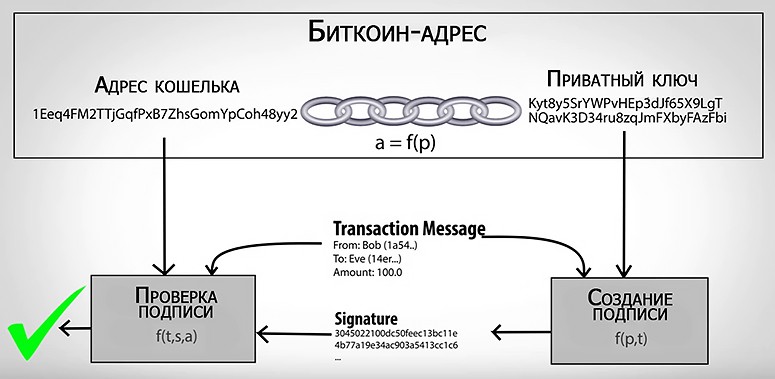
Each wallet gives the owner a unique account number. This identifier is better known as the wallet address and is a combination of randomly generated uppercase and lowercase letters and numbers. As with regular bank accounts, a bitcoin address can be shared with others to transfer cryptocurrencies to it.
An example of a public BTC address is:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
Private keys are like a password that confirms cryptocurrency transactions. This gives users access to their funds, which are held on the blockchain. Unlike public (publicly available), private codes must be stored securely with the owner.
If a user loses their public address, it can always be recovered, but on the condition that they still have access to the private key.
In cryptocurrency wallets, users can view their current balances and move coins and tokens around the blockchain system using private codes.
Security
If a user loses their private key, they will not have the secret phrase from the cryptocurrency wallet, they will lose access to all funds on the address. Thus, it is important to keep your private codes in a safe place with backups.
A cryptocurrency wallet is a software that generates and stores open and closed combinations of letters and numbers, allowing users to make bitcoin transactions. Cryptocurrency storage software is designed as mobile and desktop applications, online services or hardware devices. Wallet is a generic term for any of these implementations. In terms of security and privacy, storage for digital assets vary greatly.
Cryptocurrency wallets are designed to make it easy for coin and token holders to use their assets without having to delve into the complexities of cryptography.
The interface of any vault displays address balances, transaction histories, and account numbers that users can share with third parties to make transfers.
Bitcoin wallets are bank accounts encrypted with multi-digit numbers. If someone guesses the combination of characters of the closed code, they will have access to someone else’s bitcoins and can appropriate those funds. However, because of the gigantic numbers, the probability of this happening is practically zero.
If every person on Earth has a computer program to guess the private key in a cryptocurrency wallet, and all users make 1 billion combinations every day for 100 years, the chance that he or she will correctly name the combination of letters and numbers of the private code is 1 in ~3,512,469,265,893,923,428,170,004.
There are two layers of security that prevent attackers from discovering private alphanumeric passwords:
- Elliptic Curve Cryptography (ECC).
- Cryptographic hash functions.
Choosing a wallet with quality security and privacy practices is important. A backup feature is also necessary in case the user loses or breaks their device.
Creating a secure private key
The private code for Bitcoin and other altcoins is a series of 32 bytes. There are many ways to record this digital information:
- A string of 256 ones and zeros (32 * 8 = 256).
- Base64.
- Binary string.
- WIF.
- A mnemonic phrase.
- Hexadecimal string.
It is theoretically possible to generate a random private key for a bitcoin wallet by flipping a coin 256 times and recording the result of each attempt. Before doing so, it is worth determining which side corresponds to the value (for example, heads – 0, tails – 1, or vice versa).
In practice, you should not use this method of creating private code. Humans are not very good at generating entropy (randomness). For example, the way a user chooses to flip a coin may cause tails to fall out more often than eagles. Or perhaps the money token will have a physical imperfection that causes one side to produce more results than the other. It is best to generate the private code for a bitcoin wallet using an algorithm that provides a high level of entropy to maximize security.
Online wallet for BTC
Cryptocurrency web vaults are the least secure option for holding bitcoins. Essentially the operators of the sites own the private address codes issued by the online venues. Web wallets are more vulnerable to hackers. For example, a website or internet connection device can be tracked.
Advanced web wallet services provide a two-factor authentication feature. But it is best not to store your bitcoins in an online application at all. Nevertheless, such applications are convenient as they provide quick access to assets from any device.
Desktop wallet
These are hot vaults that contain data on a closed combination of symbols on the user’s computer. If there is no malware or other security vulnerabilities on the device, no one can steal bitcoins. However, in most cases, computers are never 100% secure. This makes desktop applications connected to the internet a target for hackers.
Paper wallet
Cold vaults that have public and private codes printed on a plain sheet of paper (often in QR form). The wallet does not connect to servers. The only way to access it is to enter the private key into any software vault or scan the QR code. Since the letter and number combinations are printed on paper, users must store the document carefully to avoid data leakage.
Swiping
Cryptocurrency users have 2 ways to transfer private code from a paper wallet to a software wallet:
- Importing (importing) stores bitcoins on the original private key.
- Sweeping sends coins to a brand new private code connected to the software wallet.
Both functions look the same, but there are fundamental differences.
When a user moves their paper wallet to a software vault, the sweeping process creates a transaction to a new public address that clears the original (paper) wallet.
Simply put, the bitcoins are sent to the software vault, which will have a different private combination of symbols. This code is presented in an encrypted form on the user’s device.
And since swiping is conducting a transaction on the blockchain, the sender is charged a fee by the miners. It is usually deducted from the balance of the cryptocurrency wallet, and the remaining amount is transferred to the wallet.
Also, unlike importing, after swiping, the funds will only be available and visible from the application where the bitcoin address from the hardcopy was placed.
It is recommended to perform swiping in the following cases:
- When someone has gained access to a private combination of paper wallet symbols.
- When the user is not sure if he/she can keep the medium (piece of paper).
- When it is necessary to destroy the paper wallet and retrieve your funds.
For better security, it is recommended to always connect cryptocurrency addresses via swiping rather than importing.
Deterministic wallet
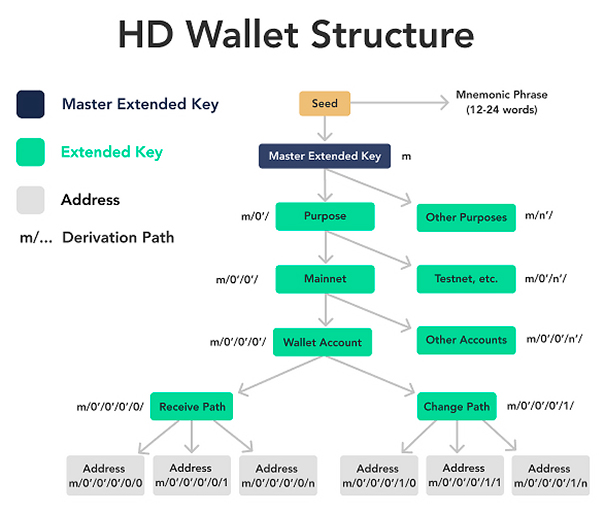
HD cryptocurrency wallets were implemented as Bitcoin’s BIP-32 standard. Prior to this, most wallets generated unlinked keys every time a user needed a new address. This Just-a-Bunch-of-Keys (JBOK) format required each character combination to be backed up individually, which was inconvenient for users. Hierarchical Deterministic Wallets (HD) can generate a backup by retaining a single original value of 64 bytes.
The algorithm creates a tree-like key structure: the vault outputs a single master code, which is used to derive child alphanumeric passwords. Each of these values can generate its own character combinations.
All generated alphanumeric passwords contain information about their depth and index – where they are located in the tree structure. The retrieval path tells the wallet how to retrieve a particular combination of characters.
This allows cryptocurrency owners to back up a single initial number instead of hundreds of codes. It is also convenient to use a parent public key (extended or xpub) to create new addresses without accessing any private codes.
Private key generation
Software for creating private alphanumeric passwords uses a form of elliptic curve-based cryptography. Bitcoin implements the secp256k1 digital signature algorithm (ECDSA). But ordinary users don’t need to understand the details to understand how this mechanism secures Bitcoin’s private codes.
The bitcoin private storage key is a very large number. When this number is multiplied by a predetermined generator point on the secp256k1 elliptic curve, a new value on the same graph is obtained. These marks become part of the public key corresponding to the private code in question. Therefore, one private alphanumeric password generates only one public cipher.
This provides 2 advantages:
- The public combination of letters and numbers can be transmitted to the network, but it is not possible to reverse engineer the private code.
- A private alphanumeric password provides digital signatures. This is how the network can mathematically prove that a particular combination of characters authenticated a particular transaction. Nodes do not need to see the content of the digital signature. All operations in the blockchain are performed according to a set principle.
The researchers noted that in the future, a theoretical attack by quantum computers could make it possible to crack ECDSA cryptography.
Transactions typically use addresses rather than public keys to increase security. This adds an extra layer of encryption.
How to store private keys for a Bitcoin wallet
Keeping hidden combinations of numbers and symbols secure comes with many risks. For example, the user may forget the code, lose the device, or be attacked by hackers. To keep hidden symbol combinations safe, you can use these tools:
- Wallets. The most common way to protect your alphanumeric passwords. There are 4 different types of wallets available: software, hardware, web-based, and paper wallets.
- Seed-phrase. Another private key encryption tool. A Seed-phrase is a chain of words containing an address that is generated by the wallet. An additional security measure to keep funds safe. If the user’s computer or smartphone crashes, you can always recover the data using the seed-phrase.
- Cryptosteel. A stainless steel tool in the form of a plate to collect codes and passwords by hand.
- Crypto Art. CryptoArt.com is a community that creates artwork consisting of an overt combination of characters on the front of the image and a hidden one on the back under a special security sticker.
Summary
In the digital world, users are vulnerable to attack by malicious actors. However, there are security measures that can mitigate the risks to keep crypto assets safe. One just needs to ensure that private keys are stored securely.
There are various tools available: offline devices, online networks, and even creative data protection tools. Each investor can choose the best way for them to secure their cryptocapital.
Frequently Asked Questions
🔑 Is it possible to manually create a private key?
It is acceptable if the user will generate the numbers randomly. But this method is not secure.
❓ Which code is created first: public or private?
According to the algorithm, a public key is produced from the private key.
💰 How many bitcoins have been irretrievably lost?
According to The New York Times, about 20% of all coins in circulation are inaccessible.
💡 How to retrieve lost bitcoins?
Find locked symbol combinations from cryptocurrency wallets.
📱 How to find out your private code?
Cryptocurrency wallets automatically generate a set of letters and numbers that you can see in the interface sections.
An error in the text? Highlight it with your mouse and press Ctrl + Enter
Author: Saifedean Ammous, an expert in cryptocurrency economics.














