Some users periodically encounter PC hangs. There are dozens of reasons for this – from trivially weak components to memory clogging. But sometimes devices start to hang because of computer viruses (malware). They can be different. For example, there are viruses that mine cryptocurrencies at the expense of the computing power of infected PCs. Such malware became popular among attackers back in the winter of 2018. Therefore, after 4 years, any user needs to know how to find a miner on a Windows 7, 10 computer in time. Otherwise, the PC may break down. There is also a risk of personal information leakage.
What is a virus-miner
A virus-miner is a malicious computer program. It uses the PC’s computing resources to mine cryptocurrency. The program works in automatic mode. At the same time, it does not notify users about the mining of coins. Therefore, it is necessary to know how to detect a hidden miner on the computer.
Principle of operation
Virus miners are created by hackers. With the help of malicious software (software), attackers leverage the resources of infected PCs to mine cryptocurrencies. The viruses mine digital coins directly on victims’ computers. The programs then automatically send the mined cryptocurrencies to the attackers’ wallets.
What is dangerous
The main risks are associated with the rapid wear and tear of computer components. Miners heavily load them. As a result, computers fail faster than in the normal mode of operation. The equipment simply cannot withstand daily mining.
Usually the following components break down:
5020 $
bonus for new users!
ByBit provides convenient and safe conditions for cryptocurrency trading, offers low commissions, high level of liquidity and modern tools for market analysis. It supports spot and leveraged trading, and helps beginners and professional traders with an intuitive interface and tutorials.
Earn a 100 $ bonus
for new users!
The largest crypto exchange where you can quickly and safely start your journey in the world of cryptocurrencies. The platform offers hundreds of popular assets, low commissions and advanced tools for trading and investing. Easy registration, high speed of transactions and reliable protection of funds make Binance a great choice for traders of any level!
- Video cards (GPU).
- Processors (CPU).
- RAM modules (RAM or DRAM).
- Cooling systems.
Computers with hidden miners can slow down a lot and hang. This is due to the high utilization of components. Due to the mining of cryptocurrency assets, the equipment does not have time to process other tasks.
Many virus miners collect information about users. They can steal photos and other files, registration data of different accounts and even cryptocurrency wallets. This leads to data leakage, loss of accounts and savings.
Ways to get infected by the virus
As of October 2022, there are 2 main methods of downloading a disguised miner:
- Downloading files from unverified sources. Often malware is embedded in pirated (unlicensed) content.
- Reading spam. Attackers also embed malware in newsletters. But in 2023, infection through spam is rare.
Usually a cryptominer is downloaded immediately with the file you are looking for. But it happens that a fraudulent utility is downloaded first. After it discreetly downloads a virus from the Internet. Such utilities do not send users notifications about downloads.
How it hides on the PC
The work of virus miners is usually controlled by remote services. They mask the programs on the PC. At the same time, the services work automatically. They themselves control the launch of software, their behavior in the system and other actions.
Viruses are usually disabled when heavy applications are launched. These can be programs for video processing, demanding games and so on. Automatic disabling of cryptominers allows infected PCs to fully spend their resources on open applications. But then the computers only temporarily work without freezes and brakes. After closing heavy applications, the malware starts functioning again.
Some remote services are tracked by system monitoring programs. Attackers set up automatic shutdown of miners if users run the software. Virus programs are “unloaded” from the list of current processes and become invisible.
The most dangerous cryptominers are able to terminate system monitoring. By doing so, they exclude their detection.
How to find a miner on your computer
Detect the software can antiviruses with updated databases. But often they find only simple malicious software. However, it is still useful to check computers for miners with antiviruses. It is recommended to do this when PC hangs suddenly appear.
It is difficult to find well-hidden cryptominers. For 2023, there are only 2 effective methods to detect them:
- Through Task Manager.
- With the help of third-party programs.
Task Manager
The Windows operating system (OS) has a built-in service for monitoring current processes. It is called Task Manager. This service allows you to monitor the load on various PC components, which is created by open applications. Also through the Manager you can:
- Configure autorun programs.
- Force applications to close.
You can open Task Manager by pressing the keyboard shortcut Ctrl+Shift+Esc, or by searching in the Start menu.
Algorithm for tracking a miner through the Task Manager:
- Start the service.
- Click “Details” in the lower left corner of the window.
- Shut down unnecessary applications through the “Processes” section. You need to close running programs, browsers and other things. Computer resources should be free.
- Sort applications by the “Graphics Processor” column. In some versions of Windows 10, it is called GPU.
- Monitor the operation of services and programs. It is better to conduct several monitoring for 10-15 minutes at different times. When checking, you can not even move the computer mouse.
If a random process with a high GPU load appears, you need to investigate its origin. You can do this through the “Details” tab. If the appeared process turns out to be a virus, it is urgent to get rid of the miner on the computer.
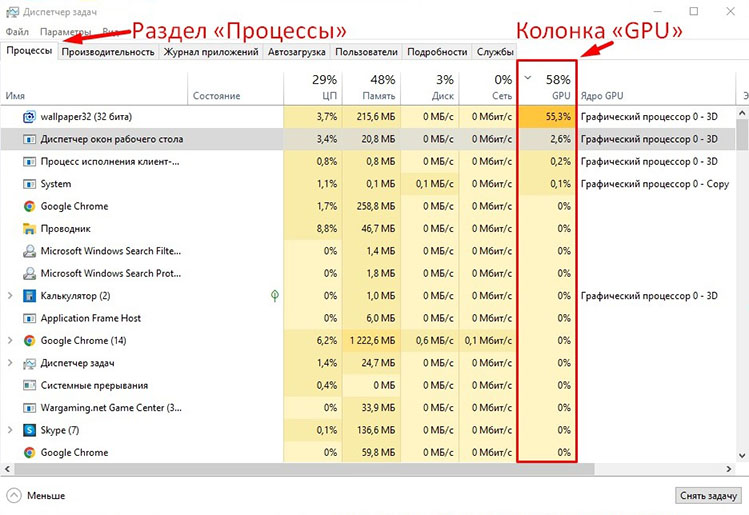
The most dangerous miners automatically shut down the service within 5 minutes on average. This is a clear sign of the presence of malware. They need to be urgently detected and removed. If you can not do it yourself, you need to give the computer to a master. It is better to contact a service center to have a specialist clean the PC from viruses.
Sometimes the dispatcher displays an abnormally high CPU load due to the browser when it is running. In other cases, this is a sign of a hidden web miner. But if you have a weak CPU installed in your computer or laptop, there is often nothing to worry about.
AnVir Task Manager
Older versions of Windows do not have a “Graphics Processor” column in the Manager. Therefore, when using such operating systems, you need to use third-party software to detect hidden cryptocurrency miners. One of the popular monitoring utilities is AnVir Task Manager. This software allows you to monitor much more data than the built-in Windows tool.
To monitor processes, you need to run the program and do not perform any actions. If activity appears in the software that heavily loads the CPU or GPU, you will need to calculate its origin. The hidden miner will need to be removed. To do this, you can use any available method.
How to remove a miner from a PC
As of October 2022, there are 3 methods of removing a miner:
- Through antivirus.
- With the help of a “curing” utility.
- Manually through the registry.
Using an antivirus is the most logical action. If it is installed on the PC, it should be applied first. But not all software determines the miners on computers. Some antiviruses can mark them as potential threats. They, too, need to be eliminated.
In the absence of an antivirus, you can use free “curing” utilities from the official websites of developers. One such software is Dr.Web CureIt! Users of various forums speak well of the program. Many note its high efficiency.
You can also remove viruses manually. To do this, first you need to recognize the miner. Then you will need to perform the following actions:
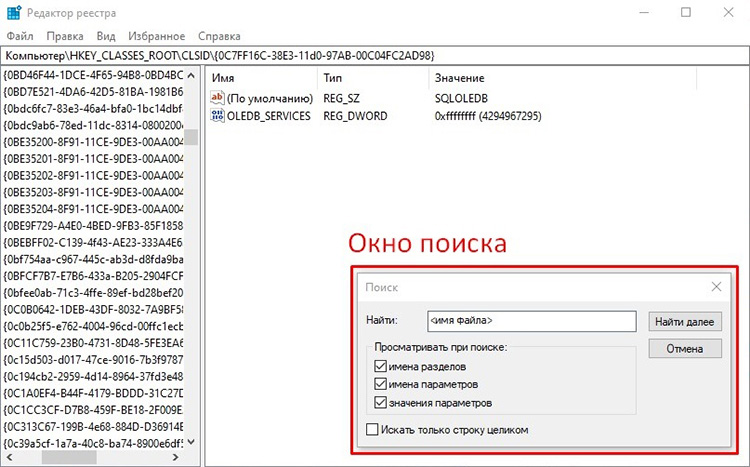
- Press Win+R on the keyboard.
- Enter the command regedit.
- Press Enter.
- Click on “Yes” in the window that appears.
- Press Ctrl+F to open a search window.
- Enter the name of the process behind which the virus-miner is hiding.
- Click “Find Next.”
- Remove all matches in the registry output.
- Restart the computer.
After the ninth step, the registry will be updated. The files of the suspected miner will be deleted. To understand the result, you will need to again monitor the computational load on the computer components through the Task Manager.
How to protect yourself from miners
The main precaution is not to download files from unverified sources. This is usually the main way of infecting computers with cryptominers.
It is not recommended to visit suspicious websites. They can download malicious programs to your computer in the background without users’ permission.
To avoid accidentally falling into fraudulent sites, you should apply web antiviruses. They warn users if the services they open are created by potential attackers.
Browser mining
Some attackers specifically develop web services to mine cryptocurrencies on the computers of Internet users. Fraudulent sites automatically start mining when you visit them. At the same time, they do not infect the computers themselves.
While the sites are open, attackers mine cryptocurrencies through visitors. This is also dangerous because of the high computational loads.
For 2023, there are 2 main methods to protect against hidden mining in the browser:
- Delicate – using extensions.
- Rough – disabling JavaScript (JS) through browser settings.
The first method is more convenient than the second. Browser extensions block suspicious scripts selectively. They constantly conduct online PC checks for miners. This ensures that the user’s experience with trustworthy sites is not disrupted.
Here are 3 examples of script blocking extensions:
- ScriptBlock – for Chrome browser.
- NoScript – for Firefox.
- ScriptSafe for Chrome.
Browser ad blockers can also help. For example, for 2023 popular extensions AdBlock and uBlock have lists of servers where hidden cryptominers work.
There are also special extensions to block browser miners. Their developers periodically update lists of hidden cryptocurrency miners. The extensions include NoCoin, MinerBlock and others.
The method with disabling JavaScript is considered rude, as it disrupts the work of many sites. Services with a large number of options often function precisely on JavaScript. Disabling the script means that sites will stop working properly. However, the method is almost 100% guaranteed to clear hidden cryptominers.
Malicious browser software codes are often written in JavaScript.
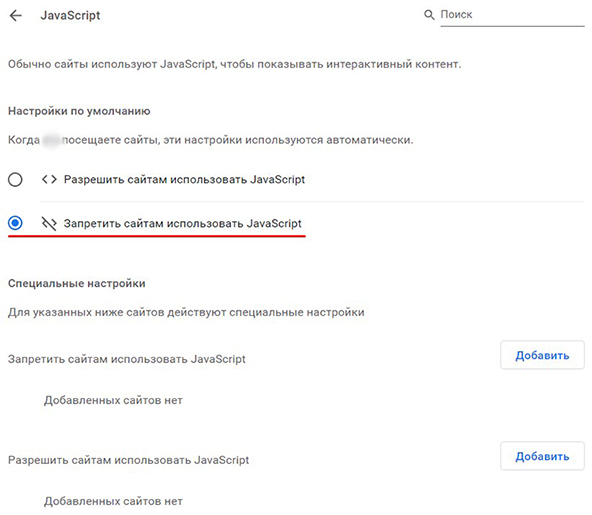
The algorithm for disabling the script using Chrome as an example:
- Launch the browser.
- Click “Customize and manage Google Chrome” (icon with 3 vertical dots in the upper right corner of the interface).
- Open the “Settings” tab.
- Go to the “Privacy and Security” section.
- Open “Site Settings”.
- Select JavaScript under “Content”.
- Click “Prevent sites from using JavaScript.”
After the seventh step, the execution of JS program codes will become prohibited in Chrome. But if necessary, you can create exceptions for reliable familiar services through the browser settings.
Programs to search for miners on PC
In 2023, there are dozens of software for monitoring system processes and detecting malware. The table below shows 3 of the most popular software that will allow the user to find and remove hidden virus-miner on their PC.
| Software name | Description |
|---|---|
| Process Explorer | This is a free utility for Windows XP and older versions of the operating system. The software was released by Sysinternals. But later Microsoft bought the rights to Process Explorer. This software works separately from the Task Manager. It allows you to find out if there is a miner on your PC and the data it uses – folders, files and others. At the same time, the software conveniently displays tasks in its own hierarchy. |
| Process Hacker | This is also a free software utility for Windows. It complements or replaces the built-in dispatcher. The advantage of the software is the display of processes in several views: simple, tree and others. At the same time, Process Hacker allows you to detect hidden applications and services. The main functions of the program are stopping, starting and uninstalling software. |
| Windows Defender | This is a free program to find and remove miners on computers. Windows Defender is an antivirus from Microsoft Corporation. In Russian, it is called “Windows Defender”. The software is installed automatically on all Windows operating systems. The program is designed to protect computers from spyware, viruses. Together with other security modules, the software automatically looks for suspicious system changes. To open the service interface, you need to go to Start – Options – Windows Update Center – Windows Security – Open the Windows Security service.” |
Summary
Hidden miners are created by cybercriminals. They need them to mine digital assets on infected PCs. Cryptominers are usually controlled by remote services. In particular, they mask malware in computer systems.
Cryptominers are dangerous. Constant high computational loads lead to rapid failure of computer components. Also, hidden programs often collect user information from infected computers.
Checklist for removing cryptominer from PC:
- Close all unnecessary applications and services.
- Run a system monitoring program.
- Detect an application that heavily loads the CPU or video card.
- Make sure that the found software is a malicious cryptominer. To do this, you need to study the system processes associated with it in detail.
- Remove the virus manually, with the help of an antivirus or a “curing” utility.
Frequently Asked Questions
😎 How to completely remove Cryptominer virus from Windows 10 computer?
Usually, “curing” utilities and antiviruses clean up all system traces of malicious software. But if there are doubts about the complete removal of the virus-miner, you can carry out the procedure manually through the registry.
❓ What is cryptojacking?
These are cybercrimes that aim to use user devices to mine digital coins.
💻 What are some dangerous virus miners?
There are a lot of them – 1.1 million malicious software. Here are 5 of the most famous ones: Coinhive, JSEcoin, XMRig, WebCOBRA and Linux.BtcMine.174.
🔴 What to do if you can’t remove the virus?
One solution is to format all computer disks. This is the most effective method.
✌ Which free antivirus is the best?
Users consider Kaspersky Security Cloud Free and Avast Free Antivirus to be among the most effective.
Is there a mistake in the text? Highlight it with your mouse and press Ctrl + Enter
Author: Saifedean Ammous, an expert in cryptocurrency economics.















