Technology has changed the way we work, communicate and financial processes. Companies and consumers are using paper money less and less. They are giving way to contactless payments. Consumers use cell phones to pay for goods online. In 2009, a new type of payment system appeared – digital money. Transfers are recorded in a public blockchain to which everyone has access. This is how the security of cryptocurrency is ensured. It is a complicated process, but the result is a digital ledger of transactions that hackers cannot hack.
What affects the security of cryptocurrency
Centralized online exchanges don’t provide the same level of protection for money as a bank. Every month there are publications about hacking trading platforms or new methods of deceiving gullible users. To avoid being among them, it is important to know the basic principles of protection from attackers and the vulnerabilities they use to access accounts.
Cryptocurrency Storage
Blockchain makes digital assets resistant to hacking. It allows you to buy and invest in cryptocurrency safely. However, more and more attacks by fraudsters are targeting its participants rather than the system itself. There are risks that need to be addressed by customers:
- The vulnerability of coins and Token stored on the exchange makes them more accessible to hackers.
- Email phishing attacks spoofing the original website with a fake one.
- Scams involving changing cell phone numbers to crack two-factor authentication.
Cold and hot wallets
The difference in the way tokens and coins are stored lies in the security level of cryptocurrency. Apps and desktop programs allow you to send and receive cryptocurrency like a digital bank account for fiat assets:
| Hot | Mobile apps |
| Desktop programs | |
| Online services (Binance, Blockchain.com) | |
| Cold | USB devices where keys are stored in encrypted form |
| Paper wallets |
Online platforms are very popular because they are easy to set up and use. When an account is created on an exchange through a mobile app or on a computer, the user has a hot wallet. This type of storage is convenient for everyday transactions. Since hot wallets are connected to the internet, it is easy to make transactions. You just need to press a few buttons on your cell phone or computer.
5020 $
Bonus für neue Nutzer!
ByBit bietet bequeme und sichere Bedingungen für den Handel mit Kryptowährungen, niedrige Kommissionen, hohe Liquidität und moderne Tools für die Marktanalyse. Es unterstützt den Spot- und Leveraged-Handel und hilft Anfängern und professionellen Händlern mit einer intuitiven Schnittstelle und Tutorials.
Verdienen Sie einen 100 $-Bonus
für neue Benutzer!
Die größte Kryptobörse, wo Sie schnell und sicher Ihre Reise in die Welt der Kryptowährungen beginnen können. Die Plattform bietet Hunderte von beliebten Vermögenswerten, niedrige Kommissionen und fortschrittliche Tools für den Handel und Investitionen. Die einfache Registrierung, die hohe Geschwindigkeit der Transaktionen und der zuverlässige Schutz der Gelder machen Binance zu einer guten Wahl für Trader jeder Ebene!
Hot wallets are easy to use, but they have one disadvantage – high vulnerability. For example, exchange accounts cannot be recommended for storing large amounts of cryptocurrency. This exposes the savings to potential security threats, hacker attacks.
For long-term investments, cold wallets are suitable. This method is considered as safe as possible, as they are not connected to the internet, and the risk of hacking is reduced. Examples include paper with keys printed on it or hardware devices. Separate physical media (usually in the form of a USB stick) are also actively used to store private keys, making them invulnerable to hackers and fraudsters.
Seed-phrase
The basic principle of cryptocurrency is the idea of decentralization. Users get an account without authenticating their identity. They don’t need to rely on a bank or other platform for secure storage. Digital currencies use the blockchain to do this. It protects them with a peer-to-peer network of computers in different locations that store copies of all the data. But decentralization has a drawback.
If the key is lost, the user cannot contact the help desk for a new code. For this purpose, a seed phrase (a list of words generated by the program that give access to digital money) is used. Its presence allows you to get control over your personal account even in case of wallet loss.
Reliable exchanges
Trading platforms store customer data in encrypted vaults.
The main attention in the choice is paid to:
- Reputation. Familiarize yourself with the history of the exchange, check cases of hacking.
- Duration of existence. Long work serves as an indicator of resistance to hacker attacks and fraud.
- Trading volume. High intensity of operations speaks of popularity.
Technical vulnerabilities
Blockchain technology is evolving, but digital currency is not immune to hacker attacks. There are cybersecurity risks that are important to be aware of. Some major companies have already been victimized by hackers and other attacks from malicious actors.
Viruses
Criminals often use malware that copies all the information that is typed in from the keyboard. It is then passed on to hackers to gain access to sites where crypto assets are stored.
Hacking a wallet or exchange
Since the existence of digital currency, many major companies have experienced fraud:
- BitGrail. An exchange platform that lost $146 million in 2018 due to a vulnerability in its servers.
- KuCoin. A crypto exchange that suffered an attack from hackers. The total damage amounted to more than $200 million.
- MtGOx. One of the first crypto platforms. Having lost $450 million, the platform ceased to exist.
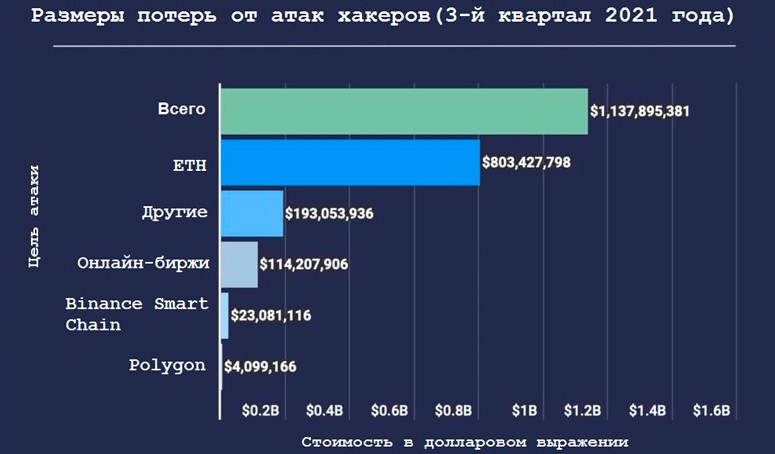
Cases of hacking a program wallet are not registered at the moment. However, if hackers manage to get information from the user (secret phrase, wallet.dat file or password), it is not difficult for them to gain access to the personal account.
Fake apps
The problem of hidden miners is common in the official Google Play and App Store. These are malicious programs that stealthily mine blocks for the victim, transferring the reward to hackers. Cases when scammers tried to distribute fake applications are not isolated. The software completely copied the design and functionality of official platforms. All the data entered by the user could be stolen by attackers to seize control of the wallet.
Fraudulent platforms
One of the ways to seize the victim’s money is to imitate the work of a crypto exchange. Often on such fake services, clients are offered great functionality with very low commissions, the platform gets high popularity among the community. When a large amount appears on the accounts, hackers transfer the funds to their wallets and close the site. The same applies to cryptocurrency pyramids offering very high profits. In reality, no investment operations are carried out, the scammers steal customers’ money.
Phishing
This is a set of actions of hackers, the main purpose of which is to obtain confidential data. Attackers make copies of official large sites, such as Binance. Links to phishing resources are distributed by sending messages via email and social networks. Less frequently, SMS to a cell phone is used. The victim, without noticing the spoofing, transfers the name, password and private electronic key himself.
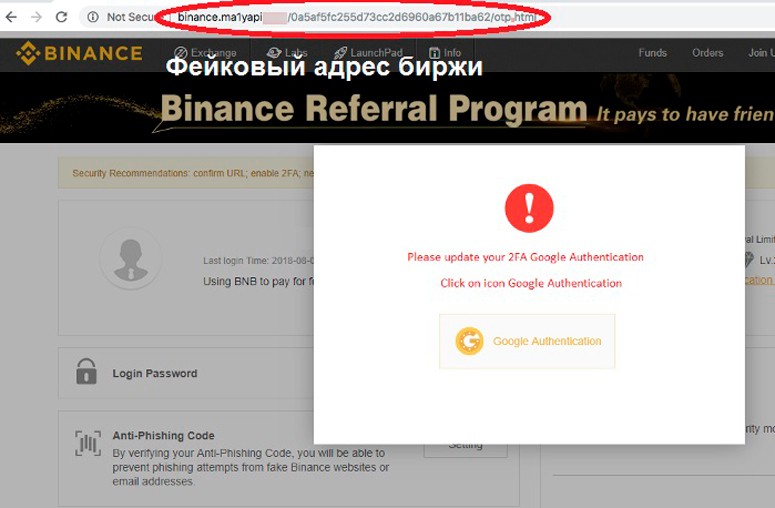
Fake social network accounts
With the development of technology, people’s communication has become available through messengers and services for communication. Hackers take advantage of this by creating fake pages.
Disguised as famous public personalities or company support services, fraudsters try to establish contact and get information. Their targets are bank card numbers, wallet addresses and passwords. Sometimes they ask to transfer an amount of money to their personal account under the cover of a fake account.
The human factor
Millions of bitcoins lie on wallets to which access will never be restored. And this has nothing to do with the actions of hackers.
Password loss
Every year, the number of “forgotten” digital coins grows. The first place among the reasons for this is the loss of a password. Since cryptocurrency works on the blockchain, and the private key file is encrypted with the SHA-256 algorithm, the probability of restoring access is close to zero. There are special services that can pick up the password. This method is suitable for those users who remember at least some part of it, but you will have to pay a large sum for the work. If the client forgot the whole password and did not save the seed-phrase, the money will be lost.
Incorrect recipient address
Transactions with digital currencies are irreversible. This means that it is impossible to return sent tokens and coins. An incorrect address or the wrong recipient network will result in a complete loss of funds. Different blockchains are usually incompatible with each other. Therefore, cryptoassets should only be sent to an address suitable for the type of money.
Many wallets already have an address verification feature. They can warn the owner about an error, but such applications do not verify the recipient’s name. If money is sent to someone else’s wallet, it will be lost.
Basic tips for cryptocurrency security
As the decentralized system grows, users far removed from the digital world are gaining access to the crypto market. In some parts of the world, bitcoin is already used as a means of payment similar to paper money. You should keep in mind the recommendations that will allow the owner to retain access to the wallet.
Use only trusted services
Many companies have been working in the crypto market for more than one year and have a good reputation. When connecting to well-known platforms, the risk of being hacked is minimized. You should carefully check the links on which the user goes to the site. If they differ even one sign from the official address of the resource, you should immediately leave the page.
Storing cryptocurrency on different wallets
Breaking the capital into additional parts is not only a matter of convenience, but also the safety of digital coins. Distributing the entire amount to several vaults allows you to save most of the money in case of loss of control over one. Hot wallets are used if the user makes many transactions, but it is not safe to use them for large sums. Cold ones are less convenient, but they are more resistant to hackers’ attacks.
QR codes when sending cryptocurrency
Transmission of details is a complicated part of the process of payment with tokens and coins. An address is a record of letters and numbers (27 to 34 characters). The recipient of the payment must provide this long set to the person who makes the transaction. To reduce errors and improve usability, you can convert the address to QR code format.
Two-Factor Authentication
2FA is an additional layer of cryptocurrency security. It allows you to make sure that the client himself is trying to access the account. First, the owner has to enter his name and password. Then the user receives a unique password on their cell phone or email. Google Authenticator application becomes a popular method of 2FA on large cryptocurrency trading platforms. The service automatically generates authorization codes and transmits them to the user’s smartphone.
Strong passwords
To protect against hacking, random (not related to the owner’s personal data) combinations of symbols, letters and numbers in different registers should be used. They allow you to ensure the security of cryptocurrency. It is recommended to set unique passwords for different resources.
Decentralized exchanges
These are platforms where participants exchange digital money without intermediaries using direct transfer (P2P). The main advantage is that tokens are held directly by the owner until the transaction is completed. This is achieved by using intelligente Verträge. High anonymity on DEX-exchanges is due to the lack of identity verification procedure. The main disadvantage – it is usually impossible to buy or sell cryptocurrency in exchange for fiat money.
Public Wi-Fi
Many cell phones have an option to automatically connect to public networks. Attackers can steal data (name, passwords, private keys) or download malware. A good solution is to stop searching for Wi-Fi after leaving work or home. If you need to get your device online in a hurry, it’s best to avoid public hotspots and never send sensitive information over someone else’s internet connection.
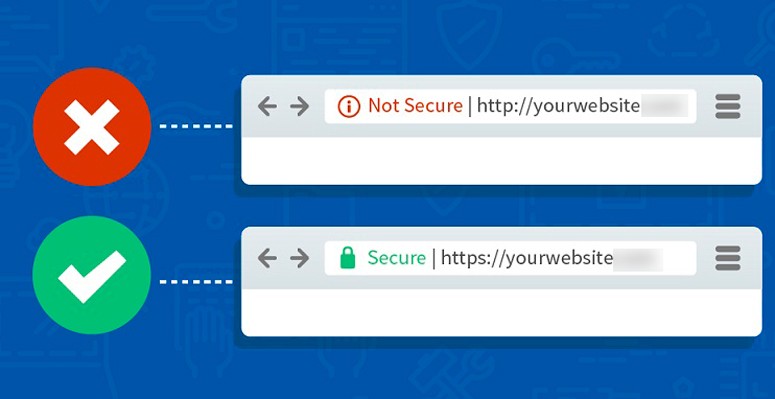
Browser search bar
To check if your connection to a website is secure, you should check the address of the page. To confirm the authenticity and security of the data transmission channel, special SSL certificates are used. If they are not installed, or the expiration date has expired, the browser can notify the user about this and block the transition to the link. It is not safe to send information and go to such a site.
Free cryptocurrency giveaways
Such promotions are called AirDrop. They are organized by public startups or large exchanges when launching a new line of business. You can get free coins for performing easy tasks:
- Publish a social media post on your behalf.
- Become a new user of the platform.
- Conduct a few transactions on it.
But under the guise of airdrops, fraudulent schemes are often used. If such an action is initiated by an unknown organizer, and it asks you to transfer money, most likely it is malicious.
Zusammenfassung
Cryptocurrency is a safe asset with a high level of resistance to hacking. Hacker attacks are most often directed at wallet holders rather than system vulnerabilities. Digital money holders need to take precautions to keep cryptocurrency safe:
- Enable two-factor authentication in account settings on exchanges.
- When clicking on links, check the page address to avoid phishing.
- Do not share passwords and other confidential information with third parties.
- Keep backup copies of keys on media that are not connected to the Internet.
- Use cold wallets to accumulate large amounts of digital money.
Despite the fact that exchanges and exchangers are fighting fraudsters, the security of cryptocurrency depends more on the owners of tokens and koins. Following simple rules by users increases the security of their data.
Häufig gestellte Fragen
✅ Can a fraudster bypass two-factor authentication?
Yes. Hackers can intercept a text message or email. To avoid this, it’s best to use the Google Authenticator app. Also, an attacker can call the victim, introduce himself as a customer service representative and ask for verification codes.
❕ How to distinguish a free coin giveaway from a fraudulent scheme?
There are special sites where information about promotions from cryptocurrency developers appears. If the invitation came to the mail or phone, and prepayment for participation is required, and there is no information about the organizer in the community, most likely it is malicious.
❓ What to do if a user goes to a phishing site and enters their data?
If the account owner realized that the service is a copy of the real one, it is necessary to change passwords to email, account, change the verification question. Any information that could give a hacker access to a personal account should be updated.
💻 How to secure your computer and cell phone from hacking?
Regularly update official software, keep an eye on the transition links in your browser, install the latest version of antivirus.
❔ What happens if a seed phrase is lost?
If the secret list of words is lost, you will not be able to restore access to your wallet. To further secure the phrase, users apply it to a durable material.
Ein Fehler im Text? Markieren Sie ihn mit Ihrer Maus und drücken Sie Strg + Eingabe
Autor: Saifedaner Ammouseinem Experten für die Wirtschaft der Kryptowährungen.















