A mining virus is a malicious program that secretly uses the computing resources of an infected device (CPU, GPU) to mine cryptocurrency for the benefit of attackers. Once on the computer via phishing attacks or infected files, the mining virus leads to increased CPU load, overheating and wear and tear of the equipment, increases power consumption and reduces system performance. It can be detected by monitoring system processes and antivirus software, and removal often requires a system cleanup or OS reinstallation.
What is a virus-miner
Miner viruses infect computers, laptops, servers and mobile gadgets. Due to the high load, the performance of the equipment for current tasks is no longer sufficient. At the same time, the following signs may appear:
- “Slows down” the work of the browser or the entire device.
- Programs or applications suddenly shut down.
- Regularly hangs the image on the screen or video failures occur.
- The built-in fan has become very noisy.
- The gadget or system unit heats up.
- Internet connection has become worse.
- Power consumption has increased, or the battery is draining quickly.
If one of the signs appeared, the cause may be common: dust in the fan, or opened a lot of “heavy” for the system applications. However, if several are marked at once, then there is a high probability that it is due to a malicious program.
Types of viruses
Trojan programs can work with or without installation into the operating system. There are also malicious extensions for web browsers and script miners on Internet sites. Protection from most of them can be provided by any antivirus. The main thing is that it should be on all the time and its databases should be regularly updated. Security utilities can already stop more than a thousand trojans. Nevertheless, new ones appear very often.
SonicWall cybersecurity developers have conducted research. The number of cryptojacking attacks from January to July 2022 increased to 67 million. The figure is 30% higher than in 2021.
5020 $
bonus for new users!
ByBit provides convenient and safe conditions for cryptocurrency trading, offers low commissions, high level of liquidity and modern tools for market analysis. It supports spot and leveraged trading, and helps beginners and professional traders with an intuitive interface and tutorials.
Earn a 100 $ bonus
for new users!
The largest crypto exchange where you can quickly and safely start your journey in the world of cryptocurrencies. The platform offers hundreds of popular assets, low commissions and advanced tools for trading and investing. Easy registration, high speed of transactions and reliable protection of funds make Binance a great choice for traders of any level!
Malware is divided into several groups. The most common among them – in the table.
| Types of programs | Description |
|---|---|
| These are console utilities for crypto-mining on the CPU or video card. Fraudsters choose coins with hidden transactions to earn money. Most often, Monero (XMR) is mined. | |
| They can be “picked up” during Internet surfing. Mining occurs on the site that opened in one of the tabs. Another option is mining on the current page. Sometimes developers openly report web mining if they use it instead of embedded advertising. In this case, visitors give their consent and share system resources. | |
| For gadgets, cryptojacking is most often implemented in games. The unsuspecting user turns it on himself. Official stores check software before publishing, so it is recommended to install software only from them. | |
| This type does not belong to hidden mining, however, it is worth mentioning. Such viruses steal passwords from accounts. The target of particularly dangerous trojans is private keys to blockchain wallets. One of them was the Mars Stealer virus, which was able to get data from MetaMask in early 2022. Before him, there was the Oski script. Therefore, you should use all methods of protection when transacting with crypto coins – for example, 2fa checks, additional blocking codes, anti-phishing phrases and regular password changes. |
Working principle
Miner viruses masquerade as system processes, start when the device is turned on, and remain active in the background. To remain undetected, they can be disabled by launching Task Manager or other monitoring utilities. Often viruses add themselves to the exclusions of antivirus programs, thus bypassing protection.
Modern mining viruses are particularly dangerous because of their ability to adapt to system loads. For example, they can temporarily suspend themselves when resource-intensive programs are running and continue mining after they are closed.
How you can get infected
What is the danger of a mining virus
Cryptojacking has replaced digital ransomware. The latter were often found in Windows of outdated versions – up to 7. Hidden mining does not directly violate laws, because it is difficult to assess what earnings were received by the fraudster. In addition to the inconvenience of using slow-moving equipment, there is a physical risk – overheating.

With an understanding of how the virus-miner works and how hashing occurs, it becomes obvious – the problem of excessive temperature is significant. A personal computer is able to cope with the load for a long time. However, the service life of components when overheating quickly decreases and can cause breakdowns. This applies to both viruses and PC maintenance. Both malware and dust should be cleaned regularly.
It is more critical if the load is on the laptop. Built-in ventilation in them is many times worse than in system units. Therefore, overheating can lead to a fire on the board. This is practically unrepairable.
Gadgets are the most sensitive to overheating. However, in this type of device, the increase in temperature is detected by the user almost immediately.
Methods of detecting a hidden miner
If suspicions are suspected, you need to check the equipment. This can be done manually or programmatically. The easiest way is to find with the help of antivirus software. Before checking, be sure to update the program’s databases to the current version. As a result, dubious processes will automatically get into quarantine and stop burdening the system.
However, if the trojan is new, it may not yet be in the databases. In this case, you will have to search for the virus manually. To get started, you need to:
- Open “Task Manager (TDM)” (key combination Ctrl+Alt+Delete) – “Processes”.
- Then evaluate if there are any suspicious programs among the current ones. To do this, alternately change the sorting in the “CPU” and “GPU” tabs of the central processing unit (CPU).
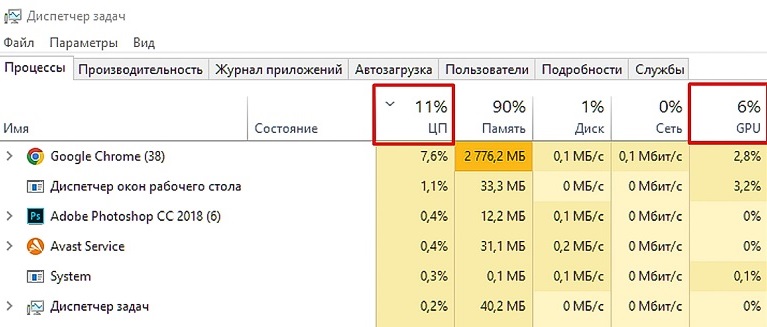
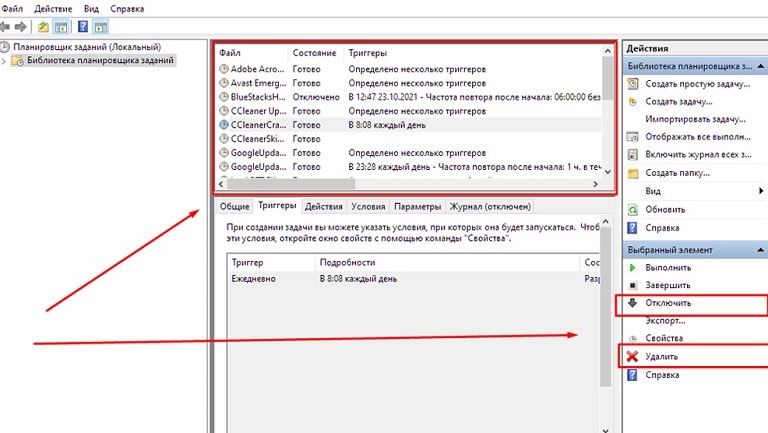
However, a check with the help of the DZ may not give results, because advanced viruses are able to shut down when it starts. In this case, you need to look in the registry for a list of autoloaders. It is located in the “Task Scheduler”. To open it, you need to perform a few steps:
- Launch the “Run” window using the Win+R combination.
- In the “Open” field, enter the command taskschd.msc – click OK.
- In the system tree, open the “Task Scheduler Library” folder.
- Select the “Triggers” tab.
This section contains scripts for automatically turning on all programs. You should check the names of suspicious processes on the Internet – it is possible that among them there will be important for system work. Then optional triggers can be disabled in the control panel, and dangerous ones can be deleted. This won’t get rid of the virus, but it will prevent it from booting automatically.
The script can prescribe the trigger again. Therefore, it is necessary to “treat” the malware. To identify programs with autorun, you can also use the AnVir Task Manager utility.
For mobile devices, software activity is monitored in the internal settings of the phone. To do this, you need to:
- Go to the section “Battery” – “Start applications”.
- Here you can manually disable automatic loading for each software.
- It is also possible to monitor the most resource-intensive utilities in the “Energy Consumption Information”.
How to remove a mining virus from your computer
Once the background cryptocurrency mining processes have been found, you need to rid the device of harmful software. You can use utilities to monitor autorun programs or antivirus software.
Each of them has weaknesses and strengths. Special software for removing virus-miner viruses is not updated as often as antivirus databases. However, it is suitable for beginners, as it can both find and destroy harmful files. Popular programs are presented in the table.
| Soft | Description |
|---|---|
| A free program from Microsoft. Can be downloaded from the official website. | |
| The software also does not require a purchase. Displays even hidden system files and services. It can both delete a process and suspend it. | |
| A powerful antivirus tool that can detect and remove various types of malware, including cryptominers. The program has a free version that allows you to perform a full system scan and remove the threats found. |
This method helps to detect and deal with the infection, but will not secure the device from future threats. Therefore, it is recommended to use antivirus systems for a full complex to fight Trojans.
The minus is that they can deactivate uninfected software, considering it a threat. In this case, you need to add the program yourself to the exceptions through the settings. Search, treatment and protection can be performed by free utilities:
- Dr.Web CureIt!
- Kaspersky Security Cloud Free.
- Avast Free Antivirus.
Each of the utilities has a manual mode: the user chooses the folder to check. The automatic variant of deep cleaning will also help to identify malware. However, checking the entire system will take more time.
The most radical way to fight viruses is to reinstall the operating system and format the hard disk. Without cleaning the files, there is a risk of leaving a malicious trojan among the saved data.
A mistake in the text? Highlight it with your mouse and press Ctrl + Enter.
Author: Saifedean Ammous, an expert in cryptocurrency economics.















